Security Assessment:
Understanding, Assessing And Mitigating Threats
In an era where data breaches and cyber-attacks are ever-present dangers, understanding the security risks your organization faces is more crucial than ever. ProCheckUp provides comprehensive services to identify, assess, and mitigate these risks, ensuring that your business remains resilient in the face of evolving threats.
1. What is Security Risk?
A security risk refers to potential threats that can exploit vulnerabilities in your system, leading to unauthorized access, data breaches, or even system shutdown. These risks can come from various sources, be it external hackers, malicious insiders, or even unintentional employee actions.

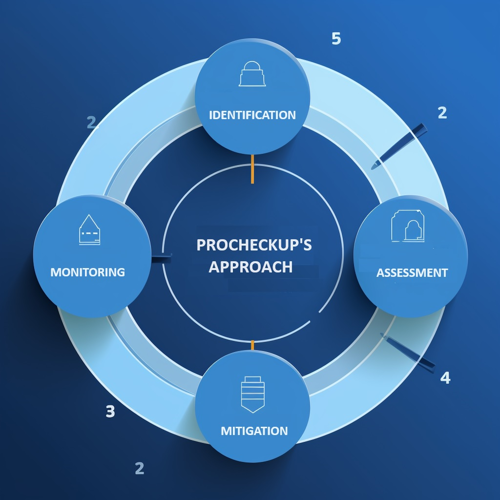
2. The ProCheckUp Approach to Security Risk
Our methodology is built upon a four-pronged approach:
- Identification: Recognizing potential security threats and vulnerabilities.
- Assessment: Evaluating the impact and likelihood of these risks.
- Mitigation: Implementing strategies to reduce or eliminate threats.
- Monitoring: Continual surveillance to identify new risks as they emerge.
![]()
3. Security Risk Identification
Using a mix of manual and automated tools, ProCheckUp scouts your digital landscape to identify potential vulnerabilities. From outdated software to weak passwords, no stone is left unturned.
Core Areas:
- Network Infrastructure
- Application Security
- Endpoint Devices
- User Behavior

4. Comprehensive Risk Assessment
Once potential vulnerabilities are identified, they are evaluated based on their potential impact on the organization and the likelihood of being exploited.
Components of Our Assessment:
- Criticality Analysis: Understanding which systems, if compromised, would have the most significant impact.
- Threat Modelling: Predicting potential attack vectors based on current vulnerabilities.
- Impact Valuation: Assessing the potential damage (financial, reputational, operational) of a successful breach
.
5. Proactive Risk Mitigation
Knowledge without action is futile. Post-assessment, ProCheckUp crafts tailored mitigation strategies to bolster your defenses and reduce vulnerabilities.
Focus Areas:
- Patch Management: Ensuring all software is up-to-date.
- Multi-Factor Authentication: Adding an extra layer of security to user logins.
- Security Awareness Training: Equipping staff with the knowledge to avoid common threats.

6. Continuous Monitoring & Response
Security landscapes are dynamic, and threats are ever-evolving. ProCheckUp employs a robust monitoring mechanism to track the emergence of new vulnerabilities and to detect potential attacks in real-time.
Key Monitoring Mechanisms:
- Intrusion Detection Systems (IDS): Identify unauthorized access attempts.
- Security Information and Event Management (SIEM): Aggregate and analyze log data for anomalies.
- Behavioral Analytics: Spot unusual user or system behaviors indicating a potential compromise.

7. Risk Communication & Reporting
Transparent communication is at the heart of ProCheckUp's approach. Our team ensures that stakeholders at every level, from IT specialists to C-level executives, understand the security risk profile and are informed of measures taken to mitigate them.
Components of Our Reporting:
- Executive Summaries: High-level overviews for decision-makers.
- Detailed Findings: In-depth reports for IT teams to action upon.
- Recommendations & Roadmaps: Future-proofing your security architecture

8. Tailored Solutions for Diverse Industries
Every industry comes with its unique set of challenges. Be it the healthcare sector, which is a hotbed for personal data, or the financial services industry, with transactional vulnerabilities; ProCheckUp tailors its security risk approach based on industry-specific nuances.
![]()
9. Stay Ahead with ProCheckUp
In a world where threats don’t sleep, neither do we. Our dedicated team of cybersecurity professionals is constantly updating their skills and tools to ensure you always stay a step ahead of potential attackers.
Benefits of Partnering with Us:
- Proactive Approach: We don’t wait for breaches to act.
- Industry Expertise: Diverse clientele gives us a unique edge.
- State-of-the-art Tools: Harnessing the latest in cybersecurity tech.

10. Ready to Fortify Your Defenses?
Take the first step towards a safer digital future. Contact ProCheckUp today and let our team guide you through understanding and mitigating your security risks.

11. Our Client Testimonials
Trust is earned, and our clients have spoken. Here's what some of them have to say about our security risk management approach and the difference ProCheckUp has made in their organizational security.
![]()

12. Case Studies in Security Risk Management
Beyond our words, our actions speak. Delve into our repository of case studies where ProCheckUp has meticulously managed and mitigated security risks for various industry leaders.
Highlights:
- Finance Sector: Tackling transactional vulnerabilities with a multi-layered defense strategy.
- Healthcare: Safeguarding patient data and ensuring compliance.
- Manufacturing: Fortifying Industry infrastructures from advanced persistent threats.

13. Our Risk Management Toolkit
At ProCheckUp, we leverage a combination of proprietary tools, state-of-the-art software, and proven methodologies to navigate the vast landscape of security threats.
- Automated Scanners: Quickly identify and categorize potential vulnerabilities.
- Threat Intelligence Platforms: Keep up-to-date with emerging threat vectors.
- Custom Scripts & Algorithms: Adapted to client-specific needs, ensuring thorough scrutiny.

14. Training & Workshops
Apart from our services, we believe in empowering our clients. ProCheckUp offers comprehensive training sessions and workshops, ensuring your in-house teams are equipped to identify and act upon security risks.
What We Offer:
- Cybersecurity Best Practices: A foundational course for all employees.
- Advanced Threat Response: Tailored for IT teams to respond efficiently.
- Simulated Attack Scenarios: Hands-on experience in a controlled environment.

15. Staying Updated with ProCheckUp
In an ever-evolving digital landscape, staying informed is the key. Subscribe to ProCheckUp’s monthly newsletter for the latest in security risk trends, tips, and our expert insights.

16. Partner with ProCheckUp
Every minute, organizations around the world face thousands of potential cyber threats. Don't become a statistic. Let's forge a partnership that prioritizes your organization's security and ensures peace of mind.

Our security Risk services range includes:
Architecture Security Review
ProCheckUp consultants will conduct a detailed review of the organisations network security goals and requirements as well as evaluating any associated security technology policies. Read more...
CREST STAR Assessments
STAR (Simulated Target Attack and Response) is a new, intelligence-led, vulnerability testing framework devised to replicate the behaviours of a real-world threat against individual clients. Read more...
Cyber Space Intelligence (CYBINT)
Comming soon !Read more...
Data Discovery
Today’s data protection regulations (GDPR) and standards (PCI-DSS) places organisations under increased pressure to demonstrate how they safeguard personally identifiable information and sensitive data. Read more...
External Internet Discovery
External Internet discovery consultancy determines the external presence of your organisation, and whether there are any applications or services which are unknown to the organisation. Read more...
Internal network discovery/mapping
Internal network discovery consultancy determines the internal presence of your organisation, and whether there are any applications or services which are unknown to the organisation. Read more...
Mergers and Acquisitions
Any Merger or Acquisition (M&A) scenario that involves integrating networks or services, with a previously unvetted organization or partner should be subject to extensive security audit first. Read more...
Onsite/Remote Security Manager
The outsourced Chief Information Security Officer (CISO) provides information security leadership from an appropriate pool of expertise and technical resources from within ProCheckUp. Read more...
Open Source Intelligence Gathering
ProCheckUp uses OSINT and online tools, to determine the organisations externally exposed networks/IP ranges. domain names and sub domain names in use.Read more...
Physical Security Audit
Physical security of Information is often an area that is overlooked with the concentration usually placed on technical controls yet safeguarding the physical environment can have a huge impact on the overall information security of an organisation. Read more...
Segmentation Testing
Network segmentation of, or isolating (segmenting), the cardholder data environment from the remainder of an entity’s network is not a PCI DSS requirement. Read more...
Targeted attack resistance assessment
Protecting your organization from sophisticated cyber threats requires a deep understanding of the tactics, techniques, and procedures employed by modern adversaries.Read more...
Virtual CISO
The outsourced Chief Information Security Officer (CISO) provides information security leadership from an appropriate pool of expertise and technical resources from within ProCheckUp. Read more...
For More Information Please Contact Us

ACCREDITATIONS






