Central Government Sector
Quick Introduction:
In an era where digital infrastructure is as critical as the physical, the central government sector stands at the forefront of a new kind of warfare—cyber warfare. With an array of digital threats ranging from espionage, sabotage, to information theft, securing the nation's digital assets is as paramount as securing its borders. Cyber-security in this sector is not only about defending against malicious attacks but also ensuring the confidentiality, integrity, and availability of government services that citizens depend upon.

Cyber-security Regulations
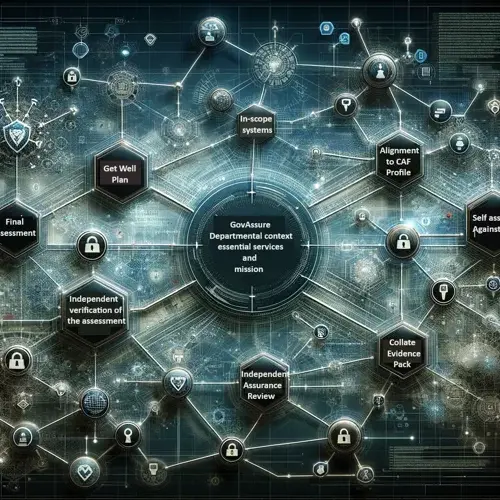
GOVASSURE:
Govassure serves as the cornerstone of the UK government's information assurance strategy, offering a standardized framework to assess and mitigate risks across various departments.
UK-GDPR: Prioritizing Data Privacy in Central Government
UK-GDPR compliance ensures that government departments are accountable for the personal data they handle, emphasizing transparency, security, and the rights of individuals.

PCI-DSS: Securing Cardholder Data
For government sectors handling transactions, PCI-DSS compliance is non-negotiable, requiring robust security measures to safeguard payment card data.

Data Protection Act 2018
The Data Protection Act 2018 providing a framework that's specifically tailored to the UK context. Central Government Departments must align with its provisions for processing personal data, with a particular focus on areas such as data subject rights, data protection impact assessments, and data sharing across borders.

Cyber Essentials:
Cyber Essentials is a government-backed, industry-supported scheme that guides organizations in fundamental cybersecurity practices, a baseline for all government bodies.

ProCheckUp Solution's
UK-GDPR Compliance:
- IASME Cyber Essentials: A certification that verifies basic cyber-security hygiene, ensuring that financial institutions have fundamental security controls in place to protect against common cyber threats. (Learn More)
- IASME Cyber Assurance: This includes a GDPR readiness assessment to ensure that all aspects of data privacy and security are addressed, thus aligning with the GDPR’s stringent requirements.(Learn More)

For Data Protection Act 2018 Adherence:
- Data Protection Impact Assessments (DPIA): Services to help government institutions conduct assessments that evaluate the impact of new projects or technologies on the privacy and security of personal data.(Learn More)
- Data Governance Consulting: Expert consultancy to ensure the correct handling of personal data across all operations, aligning with the Data Protection Act’s provisions.

For PCI-DSS Compliance:
- PCI-ASV (Approved Scanning Vendor) Services: ProCheckup, a globally recognized ASV, conducts meticulous external vulnerability scans to ensure the integrity of systems handling credit card data, in compliance with PCI-DSS requirement 11.3.2. Our ASV scan solution leverages cutting-edge security tools to rigorously test and confirm your network's defenses against known threats, helping to secure your data transactions. (Learn More)
- PCI-QSA (Qualified Security Assessor) Services: As an independent QSA firm accredited by the PCI Security Standards Council, ProCheckup embodies excellence in ensuring entities meet the stringent standards of PCI DSS. Our longstanding expertise, since the establishment of the QSA program, provides reliable validation of your compliance posture. (Learn More)
- Penetration Testing: ProCheckup's penetration testing services are an embodiment of our commitment to security excellence, meeting PCI-DSS requirement 11.4.1. Our team of Crest, Cyberscheme, and NCSC-qualified penetration testers, with a proven 24-year track record since 1999, employs a comprehensive approach to identify and remediate exploitable security vulnerabilities. (Learn More)
- Data Discovery for Primary Account Number (PAN): Our specialized services extend to the detection of PAN within your network, particularly identifying unauthorized storage locations outside the Cardholder Data Environment (CDE), adhering to PCI-DSS requirement 12.5.2. ProCheckup ensures that sensitive payment data is contained and managed securely. (Learn More)
- Segmentation Testing: With precise technical testing, ProCheckUp validates the efficacy of network segmentation, ensuring that the CDE is isolated from all systems not pertinent to card processing , in compliance with PCI-DSS requirement 11.4.5 This critical service supports PCI-DSS compliance by verifying the robustness of segmentation controls, maintaining the security of your cardholder data environment. (Learn More)
- Wireless Testing: Adhering to the stringent standards of PCI-DSS requirement 11.2.1, our team conducts comprehensive wireless testing quarterly. This process is meticulously designed to uncover and assess both sanctioned and unsanctioned wireless access points within your network, ensuring a robust security posture. (Learn More)

By integrating these cyber-security services, central government can effectively navigate the complexity of regulatory compliance while fortifying their defenses against the cyber threats that endanger the sector’s integrity and stability. These services provide a scaffold for building a comprehensive cyber-security strategy that is not just about adherence to the letter of the law but also about embedding cyber-security into the fabric of central government operations.
Maintaining Compliance
Implementing Robust Cybersecurity Frameworks
To keep up with the dynamic nature of cyber threats and regulatory requirements, central government organisations are encouraged to implement robust cyber-security frameworks that are responsive and adaptive. Here's an overview of what this involves:
- Risk Assessment and Management: Regular risk assessments to identify and prioritize potential threats, followed by the development of a risk management strategy that includes appropriate controls and mitigation tactics.
- Employee Training and Awareness: Continuous education programs for all staff members to recognize phishing attempts, manage sensitive data correctly, and understand their role in the organization's cyber-security posture.
- Incident Response Planning: A well-structured incident response plan that outlines procedures for detecting, responding to, and recovering from cyber incidents to minimize impact and resume normal operations as quickly as possible.
- Technology and Access Control: Deployment of state-of-the-art cyber-security technologies, alongside strict access controls to ensure that only authorized personnel have access to sensitive systems and data.
- Regular Audits and Compliance Checks: Conducting internal and external audits to ensure all cybersecurity measures are effective and in compliance with the relevant regulations.
- Investment in Cyber Insurance: Considering cyber insurance to mitigate financial losses from cyber incidents, which can also require organizations to maintain certain cybersecurity standards to qualify for coverage.
- Vendor and Third-Party Management: Ensuring that third-party vendors and partners also comply with cybersecurity standards to avoid breaches stemming from external sources.

Cybersecurity Process Flow Chart
![]()
Cybersecurity Collaboration and Sharing
In addition to the internal measures, it is crucial for central government organisations to actively participate in sector-wide cyber-security initiatives. These include:
- Information Sharing: Engaging in information sharing platforms such as the Financial Services Information Sharing and Analysis Center (FS-ISAC) to receive timely alerts on threats and share best practices with industry peers.
- Regulatory Engagement: Maintaining an open dialogue with regulators to stay ahead of new regulations and to influence policy development with real-world insights.
- Public-Private Partnerships: Partnering with government agencies to enhance the collective cybersecurity posture and respond more effectively to national security threats.
- Global Cybersecurity Standards: Aligning with global cybersecurity standards and frameworks, such as ISO/IEC 27001, to ensure a consistent approach to managing information security.
- Cybersecurity Advocacy: Advocating for stronger cybersecurity measures and more substantial investments in cyber-security at industry conferences and in public forums.

With these resources and strategies in place, central government providers can better anticipate and counteract the evolving cyber threats they face, ensuring trust and continuity in the digital age.
For More Information Please Contact Us

ACCREDITATIONS






