Data Protection Impact Assessments (DPIA)

A Data Protection Impact Assessment (DPIA) is a comprehensive process utilized to identify and mitigate the risks to personal data within a project. It is a critical tool for maintaining data protection compliance, especially when processing activities are likely to result in high risks to individual privacy.
DPIAs are not only a legal requirement but also an investment in the privacy and trust of the individuals whose data you are processing. They enable an organization to not only comply with the law but to demonstrate that it takes data protection seriously – an increasingly important factor in customer and stakeholder relations.
Understanding DPIAs
DPIAs serve as an essential mechanism to protect personal data, ensuring that privacy risks are identified and mitigated before projects involving personal data commence. They're not just a regulatory requirement but a proactive measure for safeguarding personal data from potential breaches and misuse.
When is a DPIA Required?
DPIAs are mandatory for processing likely to result in high risk to individuals, such as:
- Extensive profiling with significant effects
- Large-scale processing of special categories of data
- Systematic monitoring of publicly accessible areas
- Additionally, good practice dictates conducting DPIAs for any major projects processing personal data, irrespective of the perceived risk level.
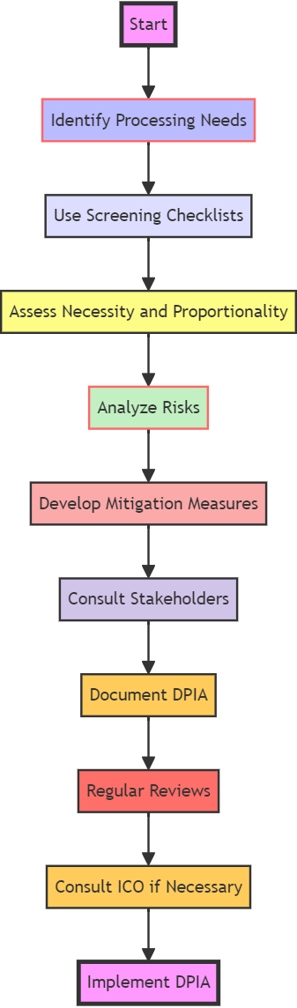
The DPIA Process
The DPIA process can be broken down into several key stages:
- Identification of Processing Operations: Understand the types of data processing your project will engage in, and determine whether a DPIA is required using screening checklists.
- Assessment of Necessity and Proportionality: Ensure that your data processing activities are both necessary for your project goals and proportionate to the data protection risks involved.
- Risk Evaluation: Analyze the potential impact on individual rights and freedoms, considering both the likelihood and severity of harm.
- Mitigation Strategy: Devise measures to reduce identified risks to an acceptable level, and incorporate these into your project plan.
- Consultation: Engage with relevant stakeholders, including your Data Protection Officer (DPO) and possibly the individuals affected, to refine your risk mitigation strategies.
- Documentation: Keep a detailed record of the DPIA process, decisions made, and measures adopted.
- Regular Reviews: DPIAs are not one-off exercises. They must be reviewed and updated regularly, especially when there are changes to the nature, scope, context, or purposes of processing.
- Regulatory Consultation: If high risks remain unmitigated, consulting the Information Commissioner's Office (ICO) before processing begins is necessary.
Regular Reviews: The Journey Continues
It is important to stress the significance of ongoing DPIA management. DPIAs are not static documents; they should evolve with the project to reflect any changes in data processing activities or the risk landscape. Here's how to ensure effective DPIA management:
- 1. Continuous Monitoring: Regularly monitor and assess the data processing activities to identify any changes that might affect privacy risks. This includes any changes in the scale or scope of the data collection, technological advancements, or shifts in regulatory requirements.
- 2. Updates and Reassessments: When changes are detected, update the DPIA accordingly. It may be necessary to conduct a new risk assessment if the changes are significant or if there is a change in the context of the processing.
- 3. Training and Awareness: Ensure that your team is trained and aware of the importance of the DPIA process. They should understand the triggers for a DPIA, such as the introduction of new processing operations or technologies.
- 4. Documentation and Record Keeping: Maintain thorough records of any changes and the rationale behind decisions made as a result of the DPIA. This documentation will be crucial for demonstrating compliance if ever challenged by data subjects or regulators.
- 5. Incident Response: Include DPIA findings in your incident response plan. Understanding the potential risks can help in prioritizing actions in the event of a data breach or other security incident.
- 6. DPIA as Part of Corporate Culture: Encourage a culture of privacy and data protection within the organization. DPIAs should not be viewed as the responsibility of a single person or department but should be part of the broader corporate governance framework.
- 7. Case Studies and Success Stories: Develop in-depth case studies that demonstrate how effective DPIA management has helped organizations mitigate risks and comply with data protection laws. Real-life examples can be very compelling, as they provide tangible proof of the value of DPIAs.
- 8. Collaborations and Guest Posts: Invite experts in the field of data protection and privacy to contribute to your content. This could take the form of guest blog posts, interviews, or co-authored white papers. Such collaborations can lend additional credibility to your content and expand your reach to the experts' followers.
- 9. Interactive Data Maps: Design interactive data flow maps that organizations can use to visualize how data moves within their systems. This can help in identifying potential privacy risks and is a useful tool for those undertaking a DPIA.
ICO page on Data Protection Impact Assessments (DPIA)
Conclusion:
Embracing Data Protection Impact Assessments (DPIAs) is a testament to an organization's commitment to safeguarding personal data, embodying a culture of security and earning customer trust. By diligently complying with DPIAs, businesses not only underscore their dedication to protecting their customers' financial information but also fortify the foundation of digital trust. This vigilant approach to data protection serves as a cornerstone in building robust customer relationships and upholding the integrity of the digital economy

For More Information Please Contact Us

ACCREDITATIONS






