Hon, ProCheckUp’s Deputy COO, had a couple of questions for the team about HAFINIUM and asked several consultants to help him understand what this fuss is all about.
Hon: So, what is going on? Who is HAFINIUM and why are they so famous?
HAFNIUM is a group of threat actors, that was identified by Microsoft as targeting governments and businesses to steal emails from organisations. The attack has now escalated with other threat actors jumping on board and been in use for months prior to patches being released. Like the SolarWinds supply chain attack, these threat actors have demonstrated aggressiveness, and brashness in leveraging flaws before the security community can react.
- - DEVCORE found an RCE on the 10th of December 2020 and duly notified Microsoft.
- - The vulnerabilities were first observed as being actively exploited in the wild on the 3rd of January 2021.
- - Microsoft released an advisory on the 3rd of March 2021 and attacks have been increasing since then with several threat actors involved including HAFNIUM.
The speed of this exploit being weaponised after the publication of the advisory serves as a stark reminder for all organisations that attackers are increasingly able to react to new zero-days and chain attacks together to go beyond the initial exploit. As Exchange servers make up a large proportion (78%) of on premise mail systems worldwide, the attack surface is very large.
Even after it became evident that this was a dangerous vulnerability being exploited, many organisations have still not patched their systems. Now is an important time to take stock, fix the breaches and review the defence in depth strategies that help to mitigate. It is becoming increasingly likely that organisations will be breached due to the speed attackers can react to vulnerabilities and leverage open-source intelligence services to find viable targets.
Hon: What is the attack background?
Microsoft and Volexity detected real-world attacks that leveraged four zero-day exploits to compromise Microsoft Exchange servers. A further update on the 3rd of March, advisory was released by Microsoft on the 5th of March stated that additional threat actors had joined the action: “Microsoft sees increased use of these vulnerabilities in attacks targeting unpatched systems by multiple malicious actors beyond HAFNIUM.”
In the attacks observed so far, the threat actor first leveraged CVE-2021-26855 RCE (Remote Code Execution) to remotely steal any user’s mailbox; Volexity stated the following conditions:
“This vulnerability is remotely exploitable and does not require authentication of any kind, nor does it require any special knowledge or access to a target environment. The attacker only needs to know the server running Exchange and the account from which they want to extract e-mail.”
The threat actors then obtained remote code execution on the Exchange server by leveraging two further vulnerabilities - CVE-2021-26858 and CVE-2021-27065. Both vulnerabilities gave an attacker the ability to write a file to any path on the server. Volexity observed: “attacker’s writing webshells (ASPX files) to disk and conducting further operations to dump credentials, add user accounts, steal copies of the Active Directory database (NTDS.DIT), and move laterally to other systems and environments.”.
Lastly, the attacker gained SYSTEM access to the Exchange server by exploiting the last vulnerability - CVE-2021-26857. This would provide the ability to steal credentials and add user accounts.
Hon: What's so bad about this?
While the full attack chain is understood to affect on-premise Exchange servers (i.e. not running in the cloud), in 2013, Exchange was running on 78% of all on-premise email servers (and that number is unlikely to have decreased, with only a few enterprise level alternatives) [1]. Given that the vulnerabilities allow unauthenticated attackers to gain remote-code execution as SYSTEM, the highest level of permissions available on Windows Servers, and that by definition, these servers have to be open to the internet, it is quickly apparent how serious these vulnerabilities can be when abused. It could be said that, in light of this ubiquity, Exchange Servers almost represent a single point of failure on a global scale.
This is further evident when considering active exploitation of the issue was reported by Volexity to have started on the 3rd of January 2021, a month before a patch was available from Microsoft [2]. To get an idea of the potential for damage, consider that at the time of writing, Shodan, the service banner search engine, reports that 250,000 servers are running Exchange worldwide, and, according to security firm Bishop Fox's CEO Mark Goodwin, 60,000 organisations have already been compromised [3].
Hon: Who does it affect?
Any unpatched Exchange servers should be considered at risk. The main targets of HAFNIUM appear to be US based government entities, law firms, defence contractors and others including private companies. This has since spread wider with additional threat actors joining in, and therefore anyone that is vulnerable may become a target.
News of this attack indicated that only on-premises Exchange servers were vulnerable; insinuating that Microsoft Office 365 cloud solution for E was impervious. However, this only appears to be the case with the CVE-2021-26855 RCE (Remote Code Execution) vulnerability. According to Volexity, this vulnerability exploits the Set-OabVirtualDirectory Exchange Powershell cmdlet, which the Microsoft official documentation states: “This cmdlet is available only in on-premises Exchange.” Therefore, it could be possible that Office 365 Exchange was vulnerable to the other three issues but were promptly patched by Microsoft.
Hon: What's at risk? What are they after?
The threat actors are after sensitive information residing inside of emails including attachments as well as the active directory NTDS.DIT file on domain controllers running Exchange server. This could provide a large cache of useful information such as legal documents, financial data for companies, staff information for use in more targeted attacks; the list is endless.
We can only speculate as to the need and end goal use of this information. However, from previous APT attacks of supposedly similar origin, the aim is to no doubt find useful individuals to target, find business critical information that can be leveraged such as technological IP, which can be manufactured quicker and much cheaper. If such an attack is indeed state sponsored, such information would allow the sponsor to leap forward technologically, especially when it comes to defence equipment research and manufacturing.
Hon: What were the four previously undetected vulnerabilities that the attack exploits?
As previously mentioned, four vulnerabilities have been addressed by Microsoft. These can be chained together to generate highly effective attack vectors, which allow threat actors to gain access to unpatched Exchange servers.
Disclosed vulnerabilities are given their own CVE (Common Vulnerabilities and Exposures) ID, which is used within the security community to define details of publicly disclosed computer security flaws. Initially, a proof of concept was available on GitHub but has since been removed; however, several threat actors may have obtained it. Currently, there is no publicly disclosed exploit code, although HAFNIUM and other threat actors are now actively targeting the vulnerabilities.
The following details the CVE’s that Microsoft released emergency patches for:
The first vulnerability, CVE-2021-26855, is a critical issue. It is an Exchange Server-Side Request Forgery (SSRF) vulnerability. SSRF attacks typically trick a web server into making arbitrary requests to a location of the attackers choosing, such as sending requests back to the server itself or other third-party systems, resulting in the server itself being compromised and allowing access to normally restricted areas, or further attacks on other systems that trust the server. In this case, attackers can send arbitrary HTTP requests which result in them being able to authenticate as the Exchange server. This gives them permission to access users’ mailboxes and read their contents. The confidentiality impact here is huge, with a clear potential for massive amounts of sensitive information disclosure.
The second vulnerability, CVE-2021-26857, is high-risk, relating to an insecure deserialisation vulnerability in the Exchange Unified Messaging service, which permits users to use voicemail and auto-attendant functions such as call answering rules. Serialisation is used in computing to convert complex data into a simpler format that can be transmitted in a stream of information from server to server, or client to server. Insecure deserialisation happens when an attacker has access to manipulate the stream via user-controllable data which is subsequently de-serialised. Exploiting this vulnerability allows code to be run as SYSTEM on the Exchange server. This could result in several other attack vectors, such as malware payloads, lateral movement to other systems and so on.
The last two issues are similar for CVE-2021-26858 and CVE-2021-27065. These are also high-risk issues which are post-authentication attacks, allowing attackers to create arbitrary files within Exchange. The ability to plant files anywhere on the file system can lead to further attacks and allow an attacker to further embed themselves in the system. An attacker’s common goal is to gain access and maintain it. By utilising the CVE-2021-26855 SSRF vulnerability or compromising a legitimate admin’s credentials via social engineering, attackers would then be able to use this attack vector.
Hon: Are there any unanswered questions so far?
While one can only speculate at this stage, an important question arises from reading the timeline posted by Volexity and the one DEVCORE released. It seems unlikely this threat actor would have found these four vulnerabilities precisely at the same time DEVCORE's researcher, Orange Tsai did. An updated timeline from Volexity demonstrates that the APT was exploiting the vulnerability before it was released to Microsoft, but after it was found by DEVCORE. How did HAFNIUM find this vulnerability? It is possible HAFNIUM caught wind of DEVCORE’s work and decided to use the vulnerability broadly before it was patched by organisations.
Hon: What remediations and mitigations are you recommending clients?
Identification of compromise and patching are key to ensuring Exchange is secured.
- 1. Checking the specific versions of patching on Exchange and immediately deploy patches to affected Exchange server versions. If you have versions equal or earlier than those listed below the server is vulnerable:
Exchange Server 2019 < 15.02.0792.010
Exchange Server 2019 < 15.02.0721.013
Exchange Server 2016 < 15.01.2106.013
Exchange Server 2013 < 15.00.1497.012
Table of CVEs affecting different Exchange versions:
|
Microsoft Exchange Version |
Affected By |
|
2019 |
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 |
|
2016 |
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 |
|
2013 |
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 |
|
2010 |
CVE-2021-26857 |
|
Older versions |
No longer supported by Microsoft |
Source: https://www.picussecurity.com/resource/blog/ttps-hafnium-microsoft-exchange-servers
- 2. If you run older servers that Microsoft no longer support, update to a later version of Exchange to ensure you are not at risk.
- 3. Consider use of cloud mail only as it was claimed not to be affected by the attack, as Microsoft have patched it already. This may not be a simple solution for larger organisations running hybrid Exchange deployments.
- 4. Consider third-party and/or encrypted mail services for highly sensitive communications.
- 5. Implement security best practices such as CIS and layered defences such as Advanced Enterprise AV with network/application, IDS/IDP, behavioural monitoring, file integrity monitoring, and log monitoring or SIEM solutions, which can help to identify and block malicious activity and may help to slow/prevent more embedded attacks from occurring beyond the initial compromise.
- 6. Use a group policy to limit actions.
- 7. Use AppLocker to prevent unsigned programs running.
- 8. For Internet exposed servers like Exchange, only allow one function. Do not run active directory, DNS, file server or SQL server on the same server. Limiting critical information exposure.
- 9. For Internet exposed servers like Exchange implement network segmentation.
- 10. Patch critical patches immediately, the industry recommendation of 30 days for incidents like HAFNIUM/WANNACRY is not sensible.
There are several methods to identify if systems have been or are likely to be compromised:
On the exchange server, check the version by running the following PowerShell script:
Get-ExchangeServer | Format-List Name,Edition,AdminDisplayVersion
Example output:
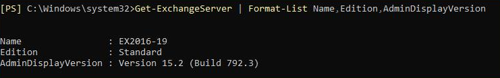
Microsoft have provided a GitHub repository with a PowerShell script to help identify post exploitation attempts. Just because you have patched the issues to prevent attackers from getting in, it does not mean that they are still not there having gained a foothold. There may be files or activity on the Exchange that may mean there is still a risk to the environment and the data.
The following script on Microsoft’s GitHub provides checks to identify indicators of compromise (IOC). To validate if you have been attacked, download it here:
https://github.com/microsoft/CSS-Exchange/releases/latest/download/Test-ProxyLogon.ps1
Example output:
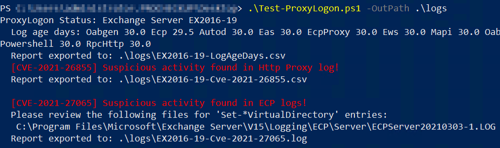
Hon: How can ProCheckUp assist clients who may be affected by this attack?
ProCheckUp can provide assistance by testing against Exchange servers to identify vulnerabilities, and forensic investigations to see if, following patching, there remain or was malicious activity from embedded threat actors.
If there has been a compromise, forensic analysis is advisable to understand if attackers have gained a foothold within the Exchange server or further into the network.
Internal infrastructure testing is also recommended to identify lateral movement methods that may be present in the environment.
Further Reading
- https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
- https://www.volexity.com/blog/2021/03/02/active-exploitation-of-microsoft-exchange-zero-day-vulnerabilities/
- https://proxylogon.com/
- https://docs.microsoft.com/en-us/powershell/module/exchange/set-oabvirtualdirectory?view=exchange-ps
References
[1] With 78% Share, Microsoft Exchange Server Largest On-Premise Email Solution, Forbes, 2013
[2] Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities, Josh Grunzweig, Volexity, 2021
[3] Microsoft Exchange Hack Could Be Worse Than SolarWinds, Maria Korolov, DataCenter Knowledge, 2021
(https://www.datacenterknowledge.com/security/microsoft-exchange-hack-could-be-worse-solarwinds)


Categories