Consumer grade and Prosumer grade 3D printers are one of the biggest things to happen in Tech for some time, they also have had one of the biggest impacts. 3D printers enable the average person not only to design and manufacture anything that the person wants, but also to customise the item and solve their unique pain point that they have been putting up with! Furthermore, others can freely download those designs and further iterate upon themselves, which up until recently has enabled a new generation access to manufacturing processes.
Nevertheless, it has also added a new vulnerability within their own network. The user is keen to further improve their new 3D printer by adding an interface such as the OctoPrint to their printer. This device adds an extra layer of convenience in the form of being able to access their 3D printer from anywhere, as well as monitoring its printing jobs; starting, stopping and pausing. However, if the device is set up incorrectly, this adds a point of entry into the user’s network and handing over potentially dangerous control of a 3D printer that prints at over 100c.
Unfortunately many of these 3D printer interfaces will be exposed to the open internet; most likely to a misconfiguration or just because the user didn’t understand the consequences of opening that device to the open internet and wanted the convenience of watching their 3D Print.
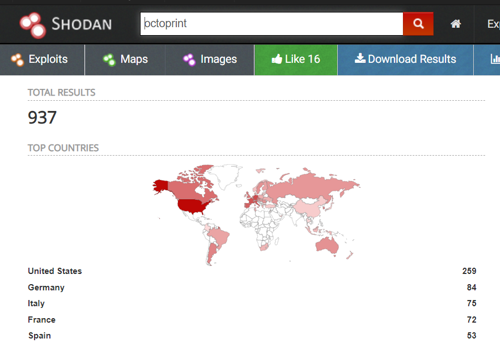
Default Credentials
In our line of work, we know that using default or weak credentials is almost like doing nothing at all. OctoPrint comes with its own default credentials which are user:pi and the password: raspberry. It is likely that many of these instances never had their password changed. Once the OctoPrint software had been set up, this provides easy access to anyone who might want to do harm in some way. An additional method to mitigate this issue is to use Basic HTTP Auth, but in my scanning, this is rarely used on exposed devices.
Let's Discuss Firmware
Many of these printers use open firmware called Marlin and this firmware has many server vulnerabilities (https://www.helpnetsecurity.com/2018/08/08/security-issues-3d-printing/) which include loading malicious G-Code (the code of the 3D item you want to print) that enabled a malicious person to take over full control of that printer directly. All this is controlled via the OctoPrint interface. With control, a malicious user would be able to make prints fail potentially doing harm to the end user of that print by giving it a flaw to make it fail or they could just turn up the heat and jam the now super-hot nozzle into the plastic giving off fumes and starting a fire.
What Can Be Done
So looking forward, it is important that the development of these interfaces and printers should set standards in how they are manufactured and how the software is developed with basic standards put in place. As of right now, no standard or regulation exists to ensure that these devices are safe to use by industry, let alone a standard user.



Categories