Red Teaming: Real-World Cybersecurity Attack Simulations

Red Teaming is a form of adversarial simulation that replicates genuine attack scenarios to test the security posture of an organisation's security infrastructure. Unlike regular penetration testing, which focuses on individual vulnerabilities, Red Teaming takes a holistic approach to assess an organization’s readiness across digital, physical, and human factors.

Why Choose ProCheckUp’s Red Teaming Services?
At ProCheckUp, our Red Teaming approach is crafted to expose and address complex security vulnerabilities that conventional testing may miss. Through realistic, intelligence-based simulations, our team offers:
- A Comprehensive Security Test: Beyond traditional tests, Red Teaming examines an organization’s ability to detect, respond to, and recover from an attack.
- Advanced Adversarial Techniques: Using TTPs from actual threat actors, our Red Team tests both technical and operational defenses.
- Detailed Remediation Insights: Each simulation concludes with actionable guidance on strengthening your defenses.
Common Questions
Red Teaming is a complex field with many facets. Here are some commonly asked questions to help demystify Red Teaming and provide clarity on its purpose and execution.
1. What is Red Teaming in Cyber-security?
Answer: Red Teaming is a practice in cyber-security where a team of experts simulate realistic cyber attacks on an organization to test and improve its defenses. It’s like a real-world security drill, probing for vulnerabilities and testing the effectiveness of security measures.
2. How Does Red Teaming Differ from Penetration Testing?
Answer: While penetration testing focuses on identifying vulnerabilities in a system, Red Teaming provides a more comprehensive approach by simulating real-life cyber attacks to test not just the digital defenses, but also physical and human security measures.
3. What is Blue Teaming?
Answer: Blue Teaming involves the organisation's internal security team, known as the "Blue Team," whose role is focused on defending against the Red Team's attacks. The Blue Team's responsibilities include maintaining daily security protocols, detecting breaches, responding to incidents, and recovering from attacks. Their ongoing task is to fortify the organization's defenses and minimize the impact of any actual breaches.s
4. Who Should Consider Red Teaming?
Answer: Any organisation that wants to rigorously test its security measures should consider Red Teaming. It is particularly beneficial for industries with high-stakes data and assets, such as finance, healthcare, government, and technology sectors.
5. How Often Should Red Teaming Exercises Be Conducted?
Answer: The frequency of Red Teaming exercises depends on various factors, including the organization’s size, nature of data handled, and changes in the threat landscape. Generally, conducting these exercises annually or bi-annually is advisable.
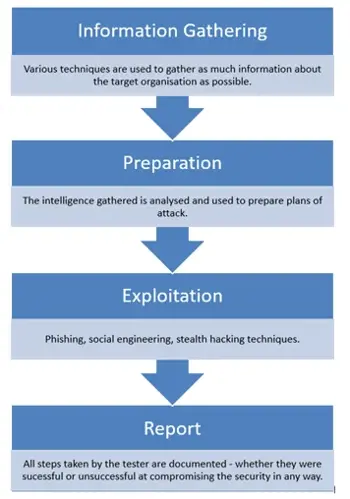
Our Red Teaming Process
Understanding the Red Teaming process is paramount for organisations endeavoring to strengthen their cybersecurity posture. This process encompasses a sequence of steps, each purposed to rigorously evaluate and subsequently enhance the defensive mechanisms of an organisation.
Information Gathering:
Every successful attack is backed by detailed intelligence, we initially focus on understanding the target. This stage finds vulnerabilities you might not even be aware of, such as unintended document leaks online or potential insider threats found by visiting social media.

Planning & Strategy:
Armed with the information gathered, ProCheckUp carefully creates attack plans tailored to the gathered intelligence.
Exploitation:
Embracing a blend of remote and on-site social engineering, stealth hacking, and phishing, our approach differs from the traditional 'noisy' penetration tests. With the objective beiing a realistic portrayal of potential stealthy or decoy attack scenarios.
Documentation & Remediation:
Every step, successful or not, is recorded. Our detailed report not only details the attack methods but provides practical remedial advice, ensuring you're better strengthened for the future..
CREST STAR Services
We take pride in being a recognized provider of CREST STAR (Simulated Target Attack and Response) services, an intelligence-based vulnerability testing framework customised to mirror real-world threat actors' actions.
For More Information Please Contact Us

ACCREDITATIONS






