IVR Security

Interactive Voice Response (IVR) systems are integral to modern business operations, serving as the first point of contact for customer interactions. These systems handle a wide range of tasks, from simple queries to complex transactions, making them critical assets that hold sensitive user data. With the increasing sophistication of cyber threats, the security of IVR systems has never been more important. This page outlines a comprehensive IVR Application Testing Methodology developed by ProCheckUp, aimed at identifying vulnerabilities and enhancing the security posture of IVR systems.
The Role of IVR in Modern Business Operations: IVR systems are pivotal in managing customer interactions efficiently. By automating the response process, they allow businesses to handle high volumes of inquiries without compromising on service quality. However, the reliance on IVR systems also introduces significant risks, as they become prime targets for cyber attacks.
The Criticality of Data Handled by IVR Systems: The data processed by IVR systems—ranging from personal identification to payment information—demands stringent security measures to protect against breaches that could lead to financial loss and reputational damage.
The Necessity for Rigorous Security Measures:As IVR technologies evolve, so do the threats against them. This necessitates a proactive approach to security, with regular testing and updates to safeguard against both known and emerging vulnerabilities.
Objectives of the IVR Application Testing Methodology: Our methodology focuses on risk identification and mitigation, aiming to fortify IVR systems against a wide array of cyber threats. It emphasizes adherence to best practices and standards, ensuring a robust defense mechanism is in place.
Customised Approach for IVR Systems: Understanding the unique challenges posed by IVR systems, our methodology is tailored to address the specific needs of voice-driven interactions, ensuring comprehensive coverage of potential vulnerabilities.
Scoping and Preparation for IVR Testing
The scoping phase is essential for defining the boundaries and objectives of the IVR testing process. It ensures that the testing aligns with the organization's requirements and regulatory standards, providing a clear framework for the assessment.
1) Purpose and Criteria
Setting clear objectives is the first step, whether it's for compliance, security audit, or incident response. The criteria for testing are aligned with the organization's risk management framework and specific data protection regulations such as GDPR or PCI DSS.
2) Application Mapping and Infrastructure Analysis
A thorough mapping of the IVR system is conducted to understand its architecture and identify potential vulnerabilities. This includes analyzing workflows, entry points, and the technology stack to ensure a comprehensive evaluation.
3) Accessibility Evaluation and Authentication
Evaluating the IVR system's accessibility and authentication mechanisms is crucial for understanding potential vulnerabilities. This involves assessing both internet-facing and internal aspects of the system.
4) Technology Stack and Environment
Identifying the technology stack and choosing the appropriate testing environment are key steps in preparing for IVR testing. This helps in understanding the system's potential weaknesses and planning the testing process to minimize operational disruptions.
5) Support and Entry Point Identification
Ensuring support from relevant teams and identifying critical entry points are vital for a successful testing process. This includes planning for immediate communication channels and incident response during the testing phase.
Testing Phases

The testing process is divided into several phases, each focusing on different aspects of the IVR system's security.
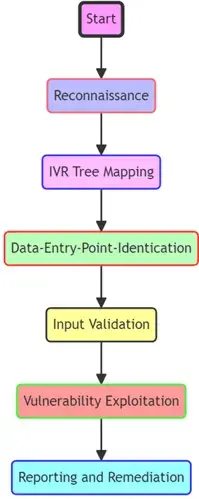
1) Reconnaissance
This phase involves gathering information about the target system without direct interaction. Techniques include public records search, DNS bruteforcing, and social engineering to understand the IVR's operational context.
2) Discovery
Mapping the IVR application's architecture and identifying data entry points are the main goals of the discovery phase. This includes documenting the IVR tree and analyzing the technology stack for known vulnerabilities.
3) Enumeration
A deeper analysis to identify specific vulnerabilities or misconfigurations in the IVR system. This phase tests for information leakage, input validation issues, and credential enumeration.
4) Exploitation
Simulating attacks based on identified vulnerabilities to assess the IVR system's resilience. This includes executing SQL injections via DTMF tones and testing for buffer overflows.
IVR Testing Techniques
This section outlines various techniques used in IVR testing, including fuzzing, buffer overflow testing, and injection attacks. Each technique is designed to uncover specific types of vulnerabilities within the IVR system.
1) Fuzzing
Fuzzing involves sending unexpected or invalid data inputs to the IVR system to identify how it handles irregular inputs. This can reveal vulnerabilities in input handling and processing logic.
2) Buffer Overflow Testing
Testing for buffer overflow vulnerabilities to see if excessive input data can lead to system compromise or denial of service.
3) Invalid Inputs and Error Handling
Evaluating the IVR system's response to invalid inputs and ensuring that error messages do not disclose sensitive information.
4) Injection Attacks
Simulating injection attacks to test if malicious commands can be executed through the IVR system, potentially leading to data breaches.
5) Brute-Forcing
Assessing the IVR's defenses against brute-force attacks aimed at guessing login credentials or PINs.
Custom Script Development
Our custom script development is tailored to the unique intricacies of each IVR system we test. By understanding the specific architecture and potential attack vectors of a system, we can create targeted scripts that simulate real-world attacks, uncovering vulnerabilities that might otherwise go unnoticed.

Ethical Considerations
Ethical considerations are paramount in conducting IVR testing to ensure that the pursuit of system security does not compromise user privacy, data integrity, or violate any legal and regulatory requirements. Adhering to these ethical guidelines ensures that testing is responsible, respectful, and legally compliant.
1) Commitment to Non-Disruption
Scheduling Tests During Off-Peak Hours: To minimise potential impacts on service availability and performance, testing is normally conducted during periods of low usage.
Use of Test Accounts and Data: Designated test accounts and simulated data are used to avoid any real user data involvement, safeguarding privacy and integrity.
2) Protecting User Data
Data Handling Protocols: Strict protocols are established for handling any real data inadvertently accessed during testing, ensuring immediate reporting and deletion in compliance with data protection laws.
Encryption of Test Data: All test data, especially if simulating real user scenarios, is encrypted and securely stored to prevent unauthorized access.
3) Consent and Authorisation
Written Approval: Testing activities are conducted only after securing written approval from the organization's leadership and legal department, clearly outlining the scope, methodology, and potential risks.
Third-party Notifications: If the IVR system integrates with third-party services, these entities are notified and their consent obtained to include their services in the testing scope.
4) Adherence to Legal and Regulatory Requirements
Compliance with Regulations: All testing activities comply with relevant regulations such as GDPR, HIPAA, or PCI DSS, ensuring the IVR system's data handling meets legal standards.
Reporting Vulnerabilities: A responsible disclosure process is followed, allowing the organization to address and remediate vulnerabilities before any public disclosure.
Reporting and Remediation
After the completion of IVR testing, a structured approach to reporting and remediation is crucial. This phase ensures that all findings are documented, prioritized, and addressed effectively to enhance the IVR system's security posture.
1) Documentation of Findings
Vulnerability Details: Each identified vulnerability is documented with details on its discovery method, and potential impact on the IVR system.
Evidence and Reproduction Steps: Supporting evidence and step-by-step instructions for reproducing the vulnerability are provided to facilitate remediation efforts.
2) Vulnerability Prioritisation
Severity of Impact: Vulnerabilities are prioritized based on their potential impact, with immediate attention given to those posing significant risks.
3) Mitigation Strategies and Recommendations
Immediate Fixes: Recommendations for quick fixes are provided to mitigate risks, such as applying patches or making configuration changes.
Long-term Remediation: Strategic recommendations are offered for preventing future vulnerabilities, including software updates and changes to development practices.
4) Remediation Timeline and Follow-up
Remediation Verification: A process for re-testing the IVR system is offered to confirm the effectiveness of the remediation efforts.
Specific Testing Requirements
To ensure a smooth and effective IVR testing process, certain prerequisites are established before the commencement of the engagement. These requirements facilitate a well-organized testing environment and clear communication channels.
Agreed Scope of Work: A detailed scope of work and authority to test are documented and agreed upon.
Single Point of Contact: A primary contact for the test is designated to streamline communication.
Testing Environment Details: If testing on-site, full site details, access restrictions, and network connectivity requirements are specified.
Test Credentials: For authenticated testing, appropriate test credentials are provided in advance.
Briefing Requirements: Any specific briefing needs, such as end-of-day debriefs, are agreed upon during the scoping phase.
Case Studies
Case Study on Fuzzing: A financial services provider's IVR system was found to improperly handle certain input sequences, allowing unauthorised access to account and card number information. Our fuzzing techniques identified these vulnerabilities, leading to prompt remediation.
Call to Action
Don't let cybersecurity concerns hold back your customer service capabilities. Take the crucial step towards securing your IVR systems today by reaching out for a comprehensive assessment. Our team is ready to provide you with the expertise and solutions needed to ensure your voice services are protected against any threat. Contact us now to safeguard your operations and maintain the trust of your customers.

For More Information Please Contact Us

ACCREDITATIONS






