What is Social Engineering? Understanding the Art of Cyber Manipulation
At its core, social engineering is a manipulative technique aimed at tricking individuals into breaking standard security procedures or divulging confidential information. Unlike traditional hacking, social engineering attacks are not necessarily technical; they exploit psychological weaknesses and the natural inclination to trust.
It is a term that encompasses a broad spectrum of malicious activities accomplished through human interactions.
This detailed guide will explore various aspects of social engineering, providing insights into its tactics, the psychology behind it, and effective defense mechanisms.

Common Tactics of Social Engineering
Phishing
- Description: Phishing involves sending deceptive emails pretending to be from trusted sources to extract sensitive information.
- Defense Strategy: Implement email filters, educate employees on recognizing phishing emails, and establish a protocol for verifying the authenticity of requests for sensitive information.

Pretexting
- Description: Attackers create a false narrative to obtain personal information. This often involves impersonation and storytelling.
- Defense Strategy: Train staff to verify the identity of individuals requesting information and to be skeptical of unsolicited requests.
Baiting:
- Description: Similar to phishing, baiting involves offering something enticing to the victim in exchange for private data.
- Defense Strategy: Cultivate a culture of skepticism and ensure employees are aware of the dangers of downloading software or opening attachments from unknown sources.
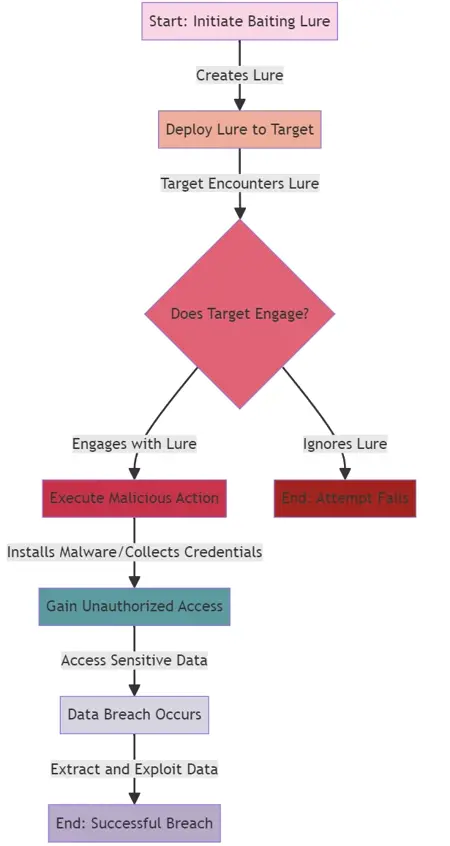
Tailgating:
- Description: Attackers gain physical access to restricted areas by following someone who is authorized to enter.
- Defense Strategy: Implement strict access control measures and educate staff about the importance of not allowing strangers to follow them into secure areas.
Quid Pro Quo:
- Description: Offering a service or benefit in exchange for information, often masquerading as a service provider.
- Defense Strategy: Establish a procedure for verifying service providers and train employees to be cautious of unsolicited offers.
Advanced Social Engineering Techniques
- Deepfake Technology and Impersonation: Understanding the threat posed by AI-generated audio and video impersonations.
- Spear Phishing and Whaling: Differentiating between broad phishing attempts and highly targeted attacks on high-profile individuals.
Understanding the Human Psychology in Social Engineering
Social engineering attacks are successful because they exploit the natural human tendency to trust. Understanding these psychological triggers is crucial in defending against these attacks:
- Manipulation Techniques: Understanding common psychological tactics used by attackers, such as authority, urgency, and fear.
- Authority: People tend to comply with requests from perceived figures of authority.
- Urgency: Creating a sense of urgency to provoke quick, less thoughtful actions.
- Social Proof: People are more likely to engage in actions that they see others doing.
Strategies to Defend Against Social Engineering
Integrating Social Engineering Awareness into Corporate Culture
- Security as a Core Value: Embedding a security-first mindset in all employees, from top management to entry-level.
- Regular Campaigns and Reminders: Keeping security awareness fresh in the minds of employees through ongoing campaigns and reminders.
Social Engineering and Insider Threats
- Identifying Potential Insider Threats: Recognizing the signs of an insider being manipulated or becoming a willing participant in social engineering schemes.
- Mitigating Insider Risks: Strategies for mitigating risks associated with insider threats, including access controls and behavioral monitoring.
Behavioral Indicators of Social Engineering Attacks
- Recognizing Suspicious Behavior: Training employees to identify unusual requests or communications that may indicate a social engineering attempt.
- Reporting Mechanisms: Establishing clear protocols for reporting suspected social engineering activities.
Tools and Resources
- Security Awareness Platforms: Utilization of platforms that offer simulated phishing tests and interactive learning modules.
- AI and Machine Learning: Use advanced algorithms to detect and alert on potential social engineering attempts.

- Security Software: Implement and regularly update anti-malware and anti-phishing software.
- Recommended Readings and Resources: Curating a list of books, articles, and online resources for employees to deepen their understanding of social engineering.

Security awareness training
Implementing robust security awareness training is key to defending against social engineering. This training should focus on:
- Defense Strategy: Regular workshops and training sessions that focus on psychological aspects, helping employees recognize and resist manipulative techniques.
- Recognizing the Signs: Educating individuals on common tactics and red flags.
- Verification Processes: Encouraging double-checking and verification before disclosing sensitive information.
- Promoting Critical Thinking: Encouraging employees to question and critically analyze requests and communications, especially those soliciting sensitive information or urgent action.
- Building a Culture of Skepticism: Cultivating an organizational culture where skepticism in the face of unusual requests is seen as a positive trait.
- Reporting Mechanisms: Establishing clear procedures for reporting suspected social engineering attempts.
- Policy Enforcement: Strictly enforce security policies and procedures.
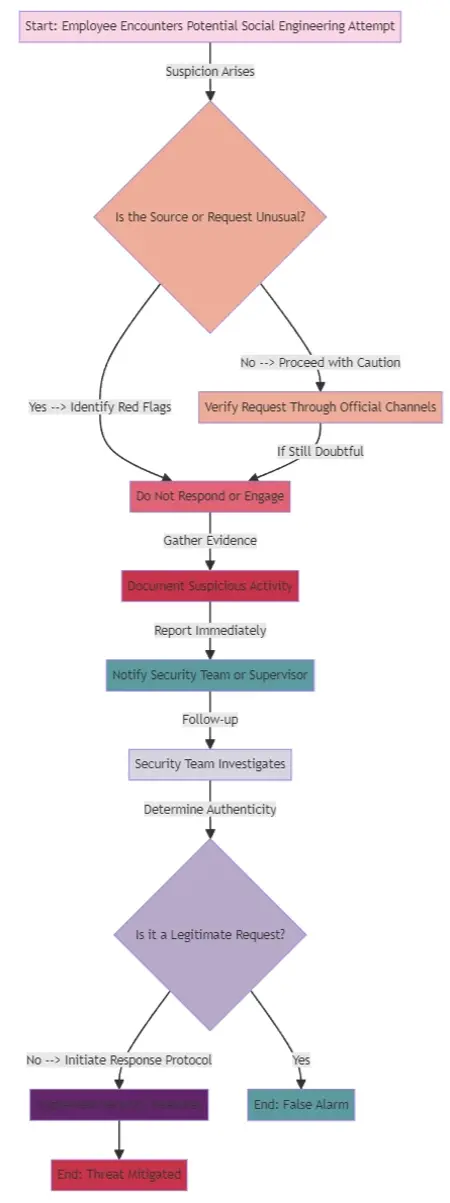
Collaborative Efforts Against Social Engineering
- Industry Cooperation: Sharing knowledge and strategies with other organizations to create a united front against social engineering attacks.
- Public-Private Partnerships: Engaging with government and law enforcement agencies to stay abreast of the latest threats and countermeasures.
Monitoring and Response
- Incident Response Planning: Having a clear plan for responding to social engineering attacks, including reporting channels and response teams.
- Continuous Monitoring: Implementing systems and procedures for continuous monitoring of suspicious activities.
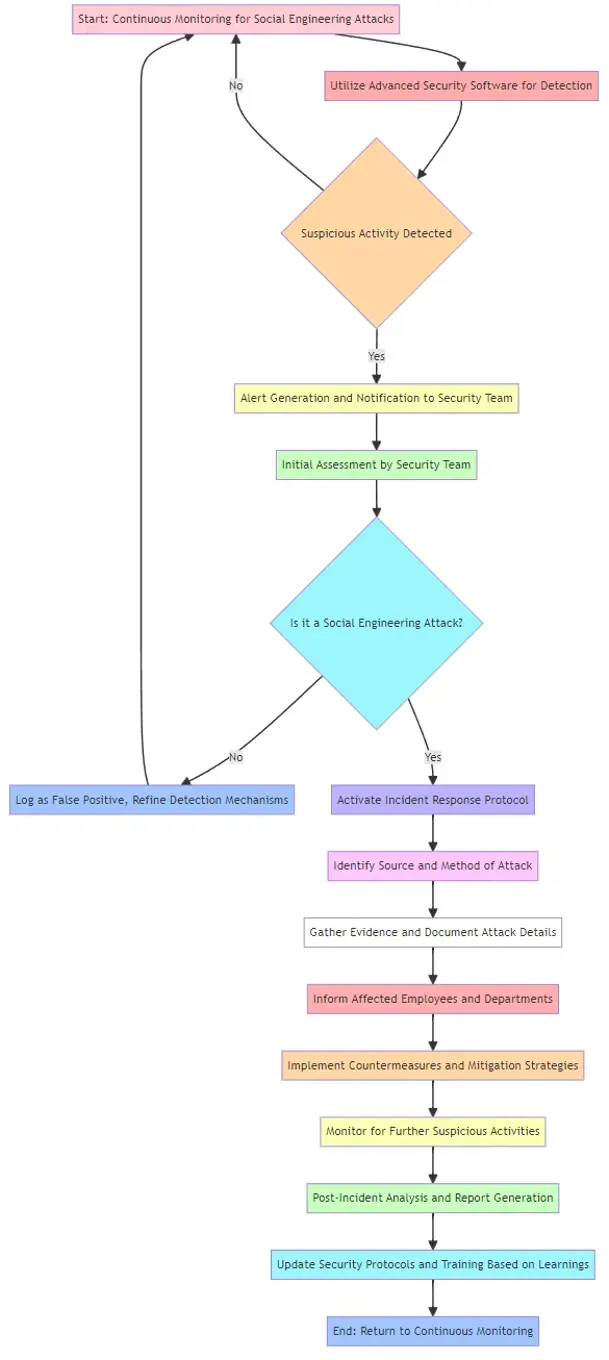
Legal and Compliance Aspects
- Understanding the Law: Familiarize with legal frameworks surrounding data protection and the implications of social engineering breaches.
- Ethical Boundaries: Setting ethical standards for countermeasures and employee monitoring.
- Policies and Procedures: Developing robust policies and procedures to prevent and respond to social engineering attacks, ensuring compliance with relevant laws and regulations.
Collaborating with Law Enforcement
- Reporting and Collaboration: Guidelines for reporting social engineering incidents to law enforcement and collaborating with them for investigations.
- Role of Law Enforcement: Understanding the role of law enforcement agencies in tackling social engineering crimes.
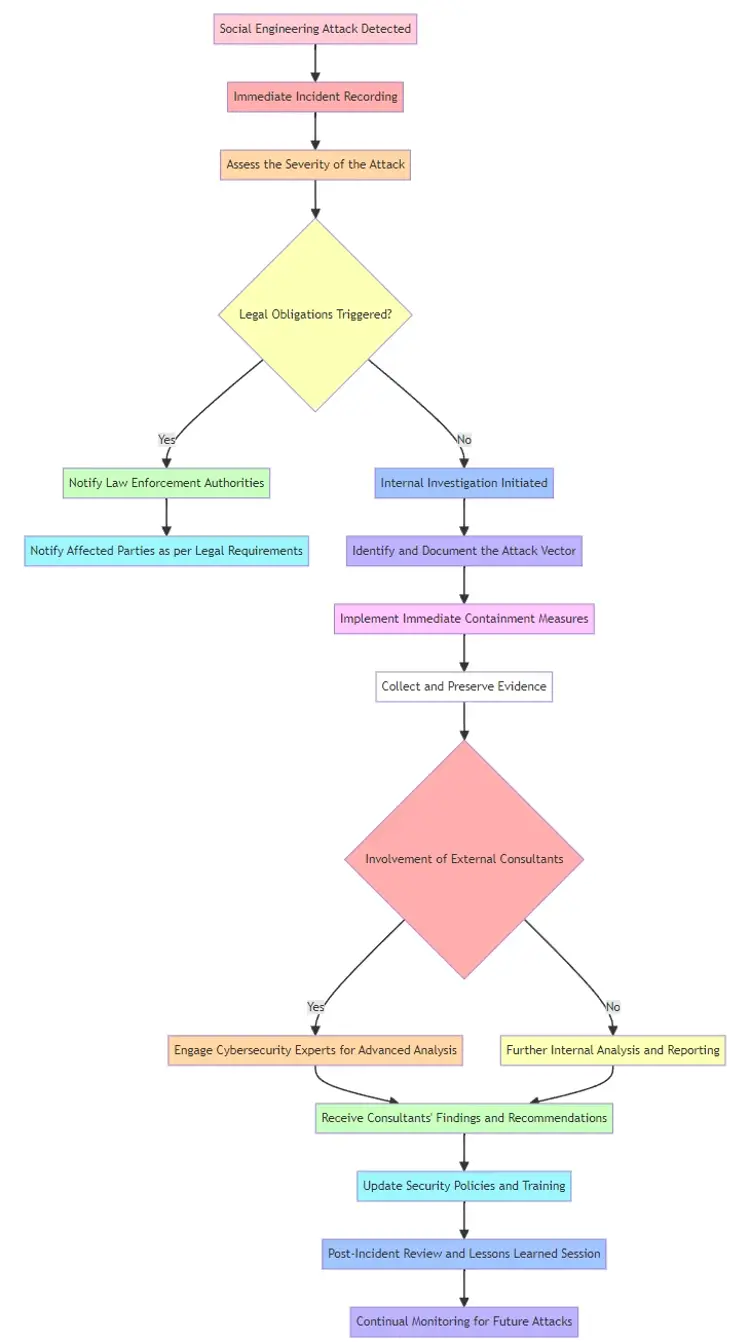
Best Practices for Remote Work Environments
- Securing Home Networks: Guidelines for employees to secure their home networks and personal devices against social engineering threats.
- Virtual Communication Protocols: Establishing secure protocols for virtual meetings and communications to prevent eavesdropping and impersonation attacks
Real-World Examples and Case Studies
Case Study 1: High-Profile Phishing Attack and Data Breach

Overview:
This case study examines a sophisticated phishing attack that compromised the personal data of millions of users from a renowned social media company. The breach not only led to substantial financial losses but also damaged the company's reputation and user trust.
Background:
The company, a household name with over 500 million users, became the target of an organized cyber-criminal group. The attackers crafted authentic-looking emails that deceived employees into revealing their login credentials.
Attack Details:
Initial Breach: The attack commenced with a series of spear-phishing emails sent to mid-level employees, purportedly from the IT department, urging an immediate password reset.
Spread and Escalation: Using the obtained credentials, the attackers gained access to the company’s internal systems, escalating their privileges to reach the data storage clusters.
Data Compromised: Personal data including names, email addresses, and encrypted passwords were ex-filtrated. The attackers also obtained access to proprietary algorithms and user behavior data.
Consequences:
- Financial Impact: The immediate financial impact included regulatory fines, compensation to affected users, and cyber-security overhaul costs totaling over $100 million.
- Reputational Damage: The breach eroded user trust, leading to a 7% user decline and a 12% stock price fall within the first month post-disclosure.
- Legal and Regulatory: The incident prompted an investigation by data protection agencies, resulting in additional fines and mandates for enhanced security measures.
Lessons Learned and Mitigation:
- Employee Education: Post-incident, the company instituted a robust cyber-security awareness program for all employees.
- Security Overhaul: Investments were made in advanced threat detection and response systems, alongside a review of access control policies.
- Regular Audits: The company scheduled frequent security audits to identify and remediate vulnerabilities.
Conclusion:
The phishing attack served as a wake-up call, showcasing the need for continual vigilance, employee training, and advanced cyber-security defenses to protect against evolving threats.
Case Study 2: Pretexting Scam Leading to Financial Loss

Overview:
This case study explores a pretexting scam where attackers impersonated vendors and tricked an organization's finance department into transferring funds to fraudulent accounts.
Background:
A medium-sized enterprise with substantial market growth over the past five years was targeted by scammers who conducted detailed background research to execute their scheme convincingly.
Attack Details:
- The Setup: Scammers gathered detailed information about the company’s vendor relationships and payment processes.
- Execution: Posing as a regular vendor, the scammers contacted the finance team, claiming a change in payment details due to 'banking upgrades' and provided new account details.
- The Breach: The finance department, failing to verify the new details, processed a significant transaction to the fraudulent account.
Consequences:
- Financial Impact: The company suffered a direct financial loss of $2.5 million, which was not recoverable.
- Operational Setback: The loss impacted the company’s operational capabilities and delayed expansion plans.
- Trust Issues: The breach of protocol led to an internal mistrust within the company, necessitating a review of processes and employee responsibilities.
Lessons Learned and Mitigation:
- Verification Processes: The company implemented a strict verification process for any changes in payment details, requiring multi-channel confirmation.
- Employee Training: Staff received training to recognize and respond to social engineering tactics.
- Enhanced Controls: Financial controls were strengthened, including the introduction of a tiered approval process for transactions.
Conclusion:
The costly incident underlined the importance of verifying financial information and maintaining a skeptical approach to unsolicited communication regarding financial transactions.
Future Trends in Social Engineering
- Evolving Techniques: Stay informed about the evolving methods used by attackers as technology advances.
- Increased Rationalization: Be aware of attacks becoming more sophisticated and personalized.
- Adaptive Defense Strategies: Continuously evolving defense strategies to stay ahead of sophisticated social engineering techniques.
Social Engineering in the Digital Age
- Digital Footprint Exploitation: Attackers use information available online to craft personalized attacks.
- Defense Strategy: Educate employees about the risks of oversharing on social media and the importance of maintaining a minimal digital footprint.

Conclusion
Social engineering remains a significant threat due to its reliance on human error rather than technological vulnerabilities. By understanding the tactics used and fostering a culture of security awareness, organizations can greatly reduce their risk of falling victim to these attacks.
For More Information Please Contact Us

ACCREDITATIONS






