The cyber threat landscape in 2024 is rapidly evolving, poised to introduce new challenges and vulnerabilities for organisations worldwide. Emerging technologies, innovative cyber attack methods, and shifting geopolitical dynamics are reshaping the battlefield of digital security. This blog post examines the most anticipated cybersecurity trends for 2024, offering insights and strategies to prepare for and mitigate these potential threats.
Table of Contents
- The Rise of AI-driven Cyber Attacks
- Ransomware: More Sophisticated Than Ever
- The Growing Threat from the Dark Web
- Malware as a Service (MaaS) and Hackers-for-Hire
- The Evolution of Phishing Attacks
- IoT and Industrial IoT Security Risks
- State-Sponsored Cyber Attacks
- Deepfakes and Advanced Social Engineering
- Zero Trust Architecture: A Necessity, Not an Option
- Cloud Security and Configuration Management
- Supply Chain Security and Third-Party Risk Management
- Adapting to Regulatory Changes and Compliance Requirements
- Investing in Cybersecurity Talent and Training
- The Importance of Incident Response and Recovery Planning
- Conclusion: A Proactive Approach to Cybersecurity in 2024
The Rise of AI-driven Cyber Attacks
2024 is witnessing a remarkable surge in artificial intelligence (AI) capabilities, transforming various sectors, including cyber-security. Unfortunately, this advancement is a double-edged sword, as cyber-criminals continue to exploit AI to orchestrate more and more complex and stealthy cyber-attacks. AI-driven attacks represent a significant shift in the cyber threat landscape, leveraging sophisticated algorithms to automate attacks, making them faster, more adaptable, and harder to detect.

Key Trends in AI-driven Cyber Attacks:
- AI-powered Phishing Campaigns: Cyber-criminals are using AI to craft convincing phishing emails and messages that mimic trusted sources. These campaigns leverage natural language processing (NLP) to generate personalized, context-aware messages, increasing the likelihood of deceiving recipients.
- Adaptive Malware: AI enables malware to analyze its environment and adapt its behavior in real-time to evade detection. This includes changing its code or exploiting new vulnerabilities, making traditional signature-based detection methods less effective.
- Automated Vulnerability Discovery: AI algorithms can scan vast networks and systems to identify vulnerabilities at a much faster rate than human hackers. Once discovered, these vulnerabilities can be exploited almost instantaneously, leaving defenders little time to react.
Mitigation Strategies:
- AI-driven Security Solutions: Incorporate AI into cybersecurity defenses. This includes behavior-based anomaly detection systems that can identify and neutralize suspicious activities that deviate from normal patterns.
- Threat Intelligence Platforms: Use AI-powered threat intelligence platforms that can analyze vast amounts of data to predict potential attack vectors and inform proactive defense strategies.
- Continuous Security Training: Educate employees about AI-driven threats. Regular training sessions can help staff recognize sophisticated phishing attempts and understand the importance of security practices.
Ransomware: More Sophisticated Than Ever
Ransomware attacks will continue to evolve, becoming a formidable challenge for organisations worldwide. Cyber-criminals are no longer content with merely encrypting data; they now engage in double and triple extortion tactics. These sophisticated strategies not only demand ransom for decryption keys but also threaten to leak sensitive information or notify the victim's clients or partners about the breach, amplifying the pressure on organisations to comply with their demands.

Evolving Ransomware Tactics:
- Double and Triple Extortion: Beyond encrypting data, attackers threaten to publish the stolen information or launch DDoS attacks, increasing the urgency and pressure to pay the ransom.
- Targeted Attacks: Instead of indiscriminate campaigns, attackers are now conducting thorough research to target specific industries or organizations that are more likely to pay larger ransoms.
- Ransomware-as-a-Service (RaaS): The emergence of RaaS platforms allows less skilled criminals to launch ransomware attacks, broadening the scope and scale of these threats.
Mitigation Strategies:
- Robust Backup and Recovery Systems: Implement regular, encrypted, and isolated backups of critical data, ensuring that recovery can be achieved without paying the ransom.
- Employee Awareness and Training: Conduct regular training sessions to educate employees about ransomware tactics and prevention measures, including spotting phishing attempts and safe browsing practices.
- Cyber Insurance: Consider investing in cyber insurance that covers ransomware attacks. This can help mitigate financial losses, although it's crucial to understand the coverage details and ensure it aligns with your risk profile.
The Growing Threat from the Dark Web
The Dark Web remains a burgeoning marketplace for cyber-criminals, offering an array of tools and services that lower the entry barrier for conducting cyber-attacks. The proliferation of no-code malware and plug-and-play attack kits enables individuals with minimal technical know-how to execute sophisticated cyber-attacks, expanding the threat landscape.

Key Concerns:
- No-Code Malware: Easy-to-use malicious software packages are available for purchase, allowing non-technical criminals to deploy malware without coding skills.
- Plug-and-Play Kits: Complete cyber-attack kits, including exploit tools and ransomware packages, are sold, simplifying the process of launching attacks.
- Organised Crime Syndicates: The Dark Web facilitates the organization and collaboration of cybercrime groups, pooling resources and sharing knowledge to execute large-scale attacks.
Mitigation Strategies:
- Dark Web Monitoring: Employ deep web monitoring services to detect if your organization's data or credentials are being traded or discussed. Early detection can prompt swift action to prevent or mitigate attacks.
- Comprehensive Cyber-security Frameworks: Implement a multi-layered cyber-security approach that includes endpoint protection, encryption, access controls, and regular security audits to reduce vulnerabilities.
- Incident Response Plans: Prepare an actionable incident response plan that includes procedures for dealing with data breaches or leaks originating from the Dark Web. This should involve legal, technical, and communication strategies to minimise the impact.
Malware as a Service (MaaS) and Hackers-for-Hire
The landscape of cyber threats is witnessing a paradigm shift with the advent of Malware as a Service (MaaS) and hackers-for-hire. These services have commoditised cyber-crime, enabling even those with minimal technical expertise to launch sophisticated attacks. This trend represents a significant escalation in the threat landscape, making cyber-attacks more accessible, customisable, and difficult to trace.

Key Trends:
- Ease of Access: MaaS platforms offer a user-friendly interface, providing a wide range of malicious services, from ransomware to spyware, readily available for purchase or rent.
- Customisation and Scalability: Customers can tailor the malware to target specific organizations or industries, increasing the attack’s effectiveness. Scalability options allow attackers to expand their operations based on success rates and financial resources.
- Anonymity and Payment: These services often operate on the dark web, offering anonymity to their users. Transactions are typically conducted in cryptocurrencies, further complicating tracking and prosecution efforts.
Mitigation Strategies:
- Layered Security Solutions: Deploy comprehensive security measures, including firewalls, intrusion detection systems, and endpoint protection platforms, to create multiple defense layers against various attack vectors.
- Regular Data Backups and Encryption: Maintain frequent and encrypted backups of critical data to ensure recovery in the event of an attack. Encryption of sensitive information adds an additional barrier against unauthorized access.
- Employee Awareness Training: Educate employees about the risks of MaaS and hackers-for-hire, emphasizing the importance of security practices such as avoiding suspicious links and reporting potential threats.
The Evolution of Phishing Attacks
Phishing attacks are undergoing a sophisticated transformation, leveraging artificial intelligence to create highly personalized and convincing campaigns. These modern phishing attacks are designed to bypass traditional security measures and exploit human vulnerabilities, emphasizing the need for advanced detection tools and comprehensive security awareness training.
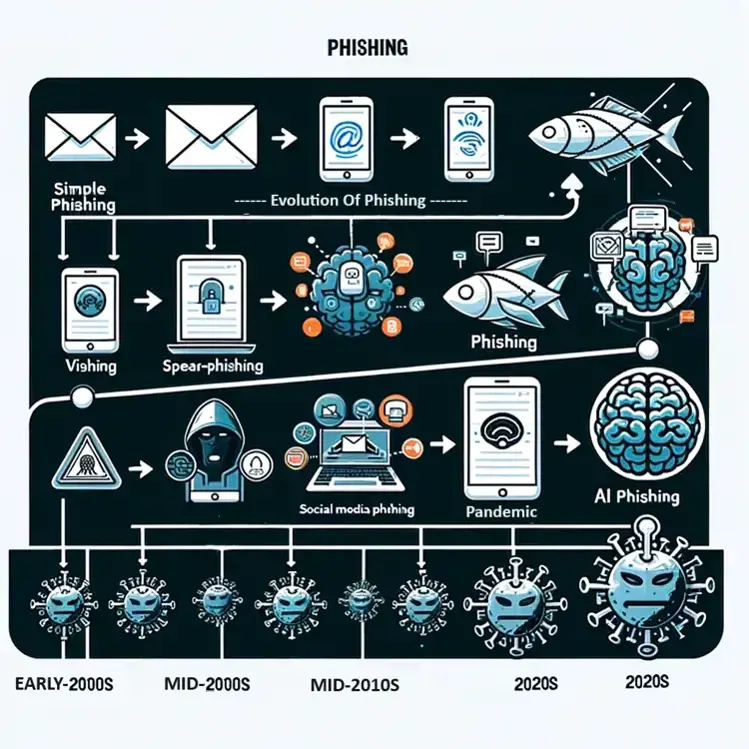
Key Trends:
- AI-driven Personalisation: Attackers use AI to analyze vast amounts of data, including social media and public records, to craft personalized phishing messages that resonate with specific targets.
- Spear Phishing and Whaling: Focused attacks on individuals or specific roles within an organization, such as executives (whaling), are becoming more common, using information that makes the fraudulent requests seem legitimate.
- Integration of Advanced Technologies: The use of machine learning algorithms to improve the success rates of phishing campaigns and the incorporation of sophisticated spoofing techniques to create nearly indistinguishable fake websites.
Mitigation Strategies:
- Advanced Detection Tools: Implement AI and machine learning-based detection systems that can analyze email content, metadata, and sender reputation to identify and quarantine phishing attempts.
- Security Awareness Training: Regular training sessions should inform employees about the latest phishing techniques, emphasizing the importance of scrutinizing email sources, links, and attachments.
- Phishing Simulations: Conduct simulated phishing attacks to test employee vigilance and reinforce training by providing real-life examples of how phishing attempts may appear.
IoT and Industrial IoT Security Risks
The exponential growth of Internet of Things (IoT) and Industrial IoT (IIoT) devices has significantly expanded the cyber-attack surface, introducing new vulnerabilities and risks. These devices, often built with minimal security features, present attractive targets for cyber-criminals looking to steal data or disrupt operations.
Key Trends:
- Expanding Attack Surface: The sheer volume of connected devices, many of which are inadequately secured, provides numerous entry points for attackers.
- Complexity of IoT Ecosystems: The interconnected nature of IoT devices means that compromising one device can potentially allow attackers to infiltrate further into the network.
- Lack of Standardisation: The IoT industry suffers from a lack of security standards and practices, leading to inconsistent security measures across devices and systems.
Mitigation Strategies:
- Secure Coding Practices: Encourage the development of IoT devices with security in mind, including the implementation of secure coding practices and regular security audits.
- Regular Software and Firmware Updates: Ensure that IoT devices are regularly updated with the latest security patches to address known vulnerabilities.
- Adoption of Zero-Trust Models: Treat all IoT devices as potential threats, applying strict access controls and continuously verifying the security status of each device.
- Network Segmentation: Isolate IoT devices on separate network segments to limit the potential impact of a compromise and restrict lateral movement within the network.
State-Sponsored Cyber Attacks
State-sponsored cyber attacks have become a critical concern for national security, corporations, and critical infrastructure. These sophisticated attacks, driven by geopolitical motives, aim to steal sensitive information, disrupt essential services, and compromise critical infrastructure. The complexity and scale of these attacks require an advanced and coordinated response strategy involving both private sector organizations and government agencies.
Key Trends:
- Targeted Attacks on Critical Infrastructure: Utilities, financial systems, and healthcare services are prime targets, with the potential for significant societal impact.
- Advanced Persistent Threats (APTs): State-sponsored actors employ APTs to gain long-term access to networks, allowing them to stealthily monitor and extract data over extended periods.
- Cyber Espionage: Intellectual property, state secrets, and sensitive government data are at risk of being stolen to gain competitive or strategic advantages.
Mitigation Strategies:
- Collaboration with Government and Law Enforcement: Establish strong ties with national cybersecurity agencies and law enforcement to receive threat intelligence and support.
- Sophisticated Cybersecurity Solutions: Deploy advanced security technologies, including AI-driven threat detection and response systems, to identify and mitigate complex threats.
- Comprehensive Incident Response Plans: Develop and regularly update incident response plans that include protocols for responding to state-sponsored attacks, ensuring swift action can be taken to mitigate damage.
Deepfakes and Advanced Social Engineering
Deepfake technology, which uses AI to create realistic fake audio or video content, is an emerging threat in the realm of social engineering. Cybercriminals use deepfakes to impersonate trusted individuals, manipulate information, and deceive targets into divulging confidential information or making unauthorized transactions.

Key Trends:
- Rise in Deepfake-Enhanced Phishing: Attackers use deepfake audio and video to impersonate CEOs and other high-profile figures in sophisticated phishing schemes.
- Misinformation Campaigns: Deepfakes are used to spread false information, affecting stock prices, damaging reputations, and influencing public opinion.
- Challenges in Detection: The evolving quality of deepfake technology makes it increasingly difficult to distinguish fake content from genuine, requiring advanced detection solutions.
Defense Mechanisms:
- Development of Detection Technologies: Invest in and deploy technologies capable of detecting deepfakes, including AI and machine learning models trained to identify inconsistencies and anomalies in video and audio files.
- Employee Education: Conduct regular training sessions to raise awareness about the use of deepfakes in social engineering attacks, teaching employees to verify the source of suspicious communications.
- Verification Protocols: Implement strict protocols for verifying the identity of individuals in sensitive communications, especially those involving financial transactions or confidential information.
Zero Trust Architecture: A Necessity, Not an Option
The adoption of a zero-trust security model has become imperative in the modern digital landscape, characterized by remote work, cloud computing, and mobile access. Zero trust operates on the principle that no entity, whether inside or outside the network, should be trusted by default. This approach minimizes the attack surface and reduces the risk of data breaches.

Key Principles:
- Least Privilege Access: Grant users and devices the minimum level of access required to perform their functions, reducing the potential impact of a compromise.
- Microsegmentation: Divide the network into secure zones to contain breaches and limit lateral movement by attackers.
- Continuous Verification: Implement continuous verification of all users and devices, utilizing multi-factor authentication, behavioral analytics, and endpoint security measures.
Implementation Steps:
- Identify Sensitive Data: Begin by identifying and classifying sensitive data and resources within the organization.
- Map the Transaction Flows: Understand how data moves within your organization to design effective control points.
- Enforce Strict Access Controls: Apply strict access policies based on user identity, device, and application, ensuring secure authentication and authorization mechanisms.
- Monitor and Analyze: Continuously monitor network traffic and user behavior for anomalies, employing AI-driven analytics for real-time threat detection and response.
Cloud Security and Configuration Management
As cloud adoption accelerates, the complexity and scale of cloud environments increase, elevating the risk of mis-configurations and security loopholes. Effective cloud security and configuration management are essential for safeguarding data, ensuring privacy, and maintaining compliance.

Key Challenges:
- Complex Cloud Environments: The multifaceted nature of cloud services, involving numerous platforms and integrations, complicates security and configuration management.
- Rapid Changes and Updates: The dynamic nature of cloud computing, with frequent updates and changes, makes it challenging to maintain consistent security configurations.
- Visibility and Control Issues: Gaining comprehensive visibility and exerting granular control over cloud environments pose significant challenges for security teams.
Strategies for Enhancement:
- Cloud Security Posture Management (CSPM): Deploy CSPM solutions to automatically identify and remediate misconfigurations and compliance issues across cloud environments.
- Infrastructure as Code (IaC): Utilize IaC for consistent and repeatable cloud environment setups, ensuring that security configurations are embedded from the onset.
- Continuous Monitoring and Auditing: Implement continuous monitoring solutions to detect unauthorized changes, vulnerabilities, and compliance deviations in real-time.
Supply Chain Security and Third-Party Risk Management
The interconnectedness of supply chains introduces significant cyber risks, with third-party vendors often becoming the weakest link. A robust third-party risk management program is vital to safeguard against breaches originating from vendors or supply chain partners.

Key Concerns:
- Vendor Vulnerabilities: Inadequate security practices among vendors can expose organizations to cyber threats, including data breaches and malware attacks.
- Lack of Visibility: Gaining insight into the security practices and compliance of third-party vendors is challenging, yet essential for overall security.
- Continuous Evolution of Threats: The evolving nature of cyber threats makes it imperative for organizations to continuously assess and update their supply chain security practices.
Mitigation Measures:
- Comprehensive Vendor Assessments: Conduct detailed security assessments of potential and existing vendors to understand their security posture and practices.
- Contractual Security Requirements: Incorporate specific security standards and requirements into contracts with third-party vendors to ensure compliance.
- Regular Monitoring and Audits: Regularly monitor the security posture of vendors and conduct audits to ensure ongoing compliance with security requirements.
Adapting to Regulatory Changes and Compliance Requirements
The regulatory landscape for cyber-security and data protection is constantly evolving, with new laws and standards being introduced globally. Organizations must navigate these changes to ensure compliance and protect themselves from legal and financial penalties.

Key Challenges:
- Keeping Up with Regulatory Changes: The pace of legislative and regulatory change requires organizations to be vigilant and adaptive.
- Compliance Across Multiple Jurisdictions: Organizations operating in multiple regions face the challenge of complying with diverse and sometimes conflicting regulations.
- Integration of Compliance into Business Processes: Embedding compliance into daily operations and business processes is essential but challenging for many organizations.
Strategies for Compliance:
- Regulatory Intelligence: Establish a process for continuously monitoring regulatory developments and assessing their impact on your organization.
- Compliance Management Platforms: Invest in technology platforms that streamline compliance management, from assessment to reporting and remediation.
- Cross-Functional Compliance Teams: Create cross-functional teams involving legal, IT, and business units to collaboratively manage compliance efforts and ensure that regulatory requirements are integrated into all aspects of business operations.
Investing in Cybersecurity Talent and Training
The cyber threat landscape's complexity and the rapid evolution of technology necessitate a skilled cybersecurity workforce. However, the gap between the demand for qualified cybersecurity professionals and the available talent pool is widening. To safeguard digital assets and infrastructure, organizations must prioritize the development and continuous education of their cybersecurity workforce.

Strategies for Workforce Development:
- Tailored Training Programs: Implement ongoing, role-specific training programs that align with the latest cybersecurity practices and technologies. This ensures that your team is equipped to tackle current and emerging threats.
- Certification and Continued Education: Encourage and facilitate the pursuit of professional certifications for your cybersecurity team. Certifications from recognized bodies can enhance skills and validate expertise.
- Cybersecurity Career Pathways: Create clear career pathways within your organization for cybersecurity roles. This can help retain talent and motivate employees through professional growth and advancement opportunities.
- Leveraging Managed Security Services: For many organizations, especially small and medium-sized enterprises (SMEs), building a comprehensive in-house cybersecurity team is challenging. Partnering with managed security service providers (MSSPs) can supplement internal capabilities, offering access to a broader range of cybersecurity expertise and technologies.
The Importance of Incident Response and Recovery Planning
In today’s digital world, the question is not if a cyber attack will occur, but when. An effective incident response (IR) and recovery plan is essential for minimizing the impact of a security breach. Preparedness can significantly reduce financial losses, reputational damage, and operational downtime.

Key Elements of Effective Incident Response Planning:
- Incident Response Team: Establish a dedicated IR team with clear roles and responsibilities. This team should include members from various departments, such as IT, legal, PR, and HR, to address all aspects of an incident.
- Communication Plan: Develop a communication strategy for internal stakeholders and external parties (customers, partners, regulators). Timely and transparent communication is critical to managing a crisis effectively.
- Regular Drills and Simulations: Conduct regular IR drills and simulations to test the effectiveness of your plan and team readiness. These exercises should mimic realistic attack scenarios to provide practical experience.
- Recovery Procedures: Define and document detailed recovery procedures to restore critical systems and data after an incident. This includes prioritizing the recovery of services based on their importance to business operations.
Enhancing Recovery Processes:
- Robust Data Backup Strategy: Implement a comprehensive data backup strategy, including off-site and cloud backups, to ensure data can be restored quickly following an incident.
- Integration with Business Continuity Planning (BCP): Align your IR plan with your organization’s broader business continuity planning. This ensures a coordinated approach to restoring business operations under various scenarios.
- Post-Incident Review: After an incident, conduct a thorough review to identify what went well, what didn’t, and why. Use these insights to refine your IR and recovery plans continually.
Conclusion: A Proactive Approach to Cybersecurity in 2024
As we look further ahead in 2024, the cybersecurity landscape presents a complex array of challenges that require a proactive and strategic approach. Organisations must remain vigilant, continuously adapting their security postures to protect against evolving threats. By investing in advanced security technologies, fostering a culture of cyber-security awareness, and implementing robust governance and compliance frameworks, businesses can navigate the threats of 2024 and beyond with confidence.
Stay tuned for further updates and insights as we continue to monitor the evolving cybersecurity landscape. For more detailed strategies and personalized guidance, consider consulting with cybersecurity experts who can help tailor your security measures to meet the unique needs of your organization.



Categories