We Are All Human
Since the birth of the Internet and rise of technology, the people of an organisation have long been the weakest link in the information security chain. We are all human; we commit mistakes. Even with the most advanced technology or sophisticated security practices, there is always the constraint of human input. Unfortunately, there are a plethora of people who are constantly attempting to take advantage of human error, whether it be through social engineering or user negligence. The former encompasses psychological manipulation techniques used to influence an individual to take an action that may or may not be in their best interests, such as divulging confidential information. And what is the number one piece of confidential information these attackers are after? Your password.
Humans Are Lazy
Passwords have historically been the most widely used mechanism for user authentication, serving as a first line of defence against those with malicious intent. As technology has advanced, more use cases for passwords have appeared, and their password requirements have evolved. Today, these requirements almost always consist of a lengthy set of characters often including numbers, special characters and a combination of upper and lower cases. The differing requirements between all the systems, devices and accounts that we all use on a regular basis makes it very hard to keep track. Given this, it is no surprise that people often set passwords that are short and/or easy to remember, write them down, or choose to re-use the same one for multiple accounts.

According to Google's 2018 survey on online security, 52% of people reuse the same password for multiple accounts, and another 13% of people reuse the same password for all their accounts. These figures are astonishingly high considering how common large data breaches are becoming, such as that which Facebook faced earlier this year, when over 500 million of its users had their personal information leaked, including Mark Zuckerberg himself. Any one of these unfortunate Facebook users that also fall into the bracket of reusing passwords now has a significant risk to their personal and potentially very sensitive information, given that their account details are now published online for all to see. It is not a difficult task to obtain these details and it is even more simple to take advantage of them. In the wrong hands, this can have a significant impact on one’s life, such as with fraud or identity theft. People may ask, “Why me?”, but why not, when you have made it so easy?
You can check whether you have been involved in a data leak in the past on the following website: https://haveibeenpwned.com/
Passwords Are Insecure
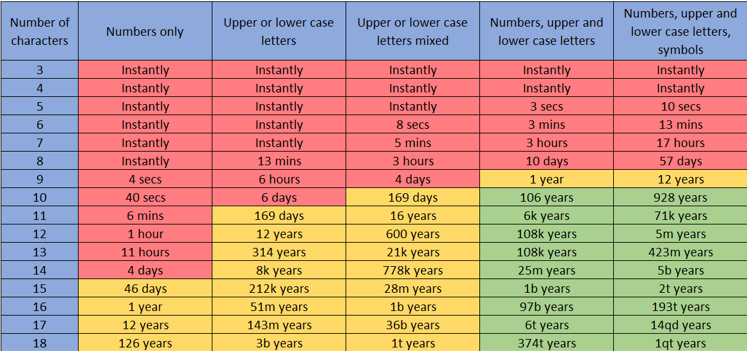
Reusing passwords is clearly not the best security practice; however, it is also important to use passwords that have a suitable balance between being easy to remember and hard for others to guess or crack. A brute-force attack is one which systematically checks all possible character combinations until the correct one is found. This type of attack requires little skill and can be performed with freely available tools. Experienced attackers can enhance brute-force attempts by noting all known information about the target, which can be fed into the attack and prioritised. For example, prioritising password combinations including known pet names, birthdays, middle names etc. will have a significantly faster success rate than simply running all combinations randomly. The table below demonstrates how quickly an attacker, or indeed, one of ProCheckUp's consultants, could crack a password based on its complexity, without any information on the target.
Add More Factors
So, what can you do? Firstly, stop using the same password for multiple accounts. This is an easy way to end up on the phone cancelling credit cards.
Secondly, add more factors. Multi-factor Authentication (MFA) requires a user to present two or more pieces of evidence to an authentication mechanism, comprising of something you have (hardware token, bank card), something you know (password, PIN), and something you are (fingerprint, eye iris, voice). MFA significantly increases levels of security as if at least one of the components is missing or incorrect, the user’s identity will not be established and access will remain blocked. When it is available, it should be used. The more factors, the better.
And lastly, it is easy to keep a secure database of passwords these days. There are a multitude of options to choose from, such as KeePass. All your passwords can be different and incredibly complex as there is no need to remember them, mitigating against brute-force attacks. Just ensure the database is kept secure – which can be done with Multi-factor Authentication.


Categories