DNS-Over-HTTPS or DoH is a relatively new protocol, which can provide a more secure browsing experience, as it encrypts and sends all DNS queries via the well-known HTTPS protocol.
DNS has been in use since the early days of the Internet, it is ubiquitous and essential for browsing, but the protocol remains largely unencrypted. This has been open to manipulation by ISPs, nation states, and anyone in the path of the unencrypted traffic such as on Wi-Fi networks.
Recently some of the major browser vendors have taken steps to try to secure the protocol using DoH, and some such as Mozilla’s Firefox and Google’s Chrome already support it. However, the attempt has become contentious for several reasons, and not everyone is happy about it.
The DoH approach essentially takes away a well-established control plane used by domain name filtering and proxy systems used to help prevent access to malicious sites. Some argue that the new approach will weaken cyber security as DoH can facilitate a bypass of enterprise policies and hamper systems reliant on DNS filtering thereby reducing the effectiveness of tools to protect users from malware. Perhaps most concerning is that these protective measures can aid criminals. Government agencies tracking malicious, criminal and terrorist activity, as well as the Internet Watch Foundation have expressed concerns as their efforts to secure us may be impeded.
This does help protect an Internet user’s privacy but there are valid criticisms that it does not fully protect people from being tracked. These include the fact that there are other means of tracking activity. Even with HTTPS there are parts of HTTPS packets with data points which can be used, such as the SNI fields and OCSP connections.
The introduction of DoH into recent versions of the Google and Mozilla browsers has caused issues in the UK and the US. In the UK the Firefox browser will no longer have the feature enabled by default for example, although it can still be turned on.
In addition, and worth considering; the new protocol necessitates a compliant DNS resolver which means that the trust and responsibility for handling the secured requests goes to these providers. Mozilla has partnered with Cloudflare for this purpose so early adopters can use this service. Currently there aren't that many resolvers out there yet, but the list is growing.
DoH will secure DNS queries and thus provide another layer of protection whilst browsing, and there is nothing wrong with trying to be more secure, but it should not be assumed to be the one and only solution to prevent tracking entirely, nor fully secure your browsing experience. DoH also helps secure and obscure bad actors’ activities, so there is something of a catch 22, but this is true of many security mechanisms. In the short term at least, it could make it harder for sysadmins, ISPs, and other agencies and vendors to run parental control, and other systems that rely on DNS visibility, but this will likely lead to better threat detection mechanisms and drive additional alternatives in future. Currently Mozilla have settled on an approach to respect user parental control and enterprise configuration choices, which should help to avoid major disruption.
About DNS
DNS or the Domain Name System is not a new concept and has remained relatively unchanged since the inception of the Internet. Whenever you visit any URL in your browser, DNS is busy in the background. It is used to translate the name of the website you enter in the browser to an IP address, so that a router can work out the which webserver your browser needs to connect with.
Because it generally just works, it is a largely unseen, and rarely thought about, but is a critical part of our daily web browsing experience. People take for granted that DNS is insecure as the lookups it performs are sent unencrypted and can be sniffed by well positioned third parties.
ISP's are required to keep this data for a period, and it can be used to provide useful services such as filtering/black lists to protect from malicious sites, but ISPs are also known to use the information as a revenue stream, selling it to marketing companies to produce targeted ads. Another example includes anti-competitive tactics, such as bandwidth limiting certain sites, or diverting users to alternative sites to those they wanted to reach. In the UK, EU legislation for net neutrality prevents this practice but this is not the case everywhere.
What is DNS over HTTPS?
DNS-over-HTTPS or DoH is a new standard based on RFC 8484 and addresses the unencrypted transmission of DNS lookups by sending requests and handling DNS responses over HTTPS. For more information, please see: https://tools.ietf.org/html/rfc8484.
The standard is still evolving and support for DoH is not yet available in native operating systems, but some browsers have support for it, and the protocol works at the application level, meaning newer applications could support DoH separate to an OS' DNS settings. This means that DoH could potentially bypass local ISP traffic filters and access blocked content, although this will be possible to be overridden in certain environments, such as businesses, schools, libraries and so on.
In order to function the DoH client needs a DNS resolver. Currently there aren't many public ones. Cloud services are available for example via Cloudflare. For a list of DNS Resolvers, please see: https://github.com/curl/curl/wiki/DNS-over-HTTPS#publicly-available-servers.
How to enable DoH
If you are interested in trying DoH or just want to be that bit more secure, and don’t mind pushing your traffic to another third party, you can enable it by doing the following:
- Mozilla Firefox
If you are using Mozilla they have had support for it for some time but it's not on by default in the UK. It is recommended to have the latest version installed. To enable DoH, do the following:
1 - Open Firefox
2 - Go to the menu icon on the top right, and select options
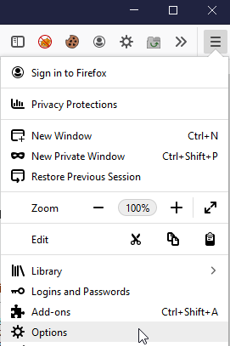
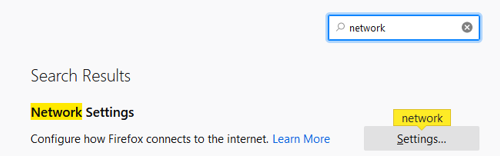
3 - Filter for Network Settings, and click the Settings box
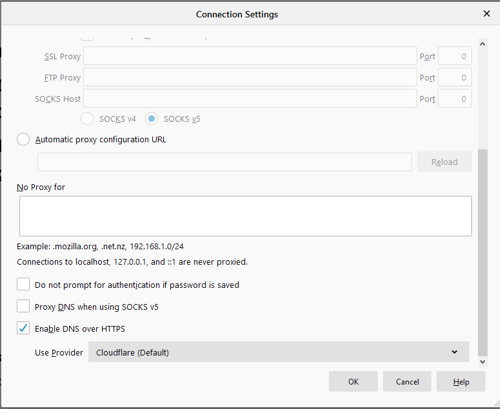
4 - In the connection settings dialogue box, scroll to the end and select Enable DNS over HTTPS, then click OK.
- Chrome
To setup support within Chrome you will need release 78 or higher. It is recommended to always get the latest version.
1 - Open Google Chrome
2 - Type chrome://flags in to the browser and press enter
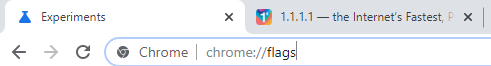
3 - Search for ‘dns’, or scroll down to find Secure DNS lookups
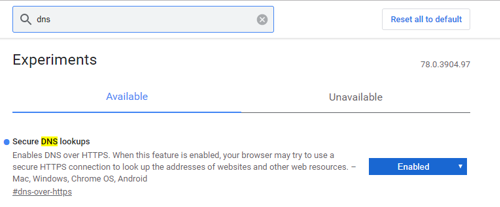
4 - Set the drop down to Enabled, which will force a restart of the browser.
Testing
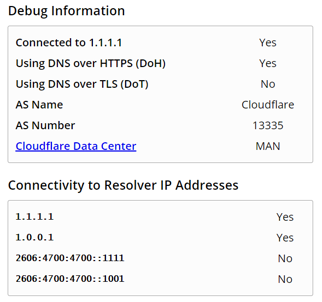
To test your DoH on either browser you can visit https://1.1.1.1/help which will confirm if it is working:


Categories