Here at ProCheckUp we have looked at the results of several digital forensics cases that we have been actively involved with and we have concluded that the use of anti-forensics is on the rise. Both on cases involving mobile devices (phones and laptops) as well as desktop devices (corporate PCs) there is evidence to support this.
Digital forensic is the process of obtaining, analysing and using digital evidence in investigations or criminal proceedings in a repeatable and scientific way. Anti-forensics focuses on hiding any incriminating digital activity by using countermeasures to forensic analysis.
A perpetrator with some understanding of how a computer system works, can study the tools and techniques available to digital forensic investigators and law enforcement. Armed with this knowledge they then can try to hide any incriminating digital activity in the same way that a burglar would try to cover their tracks by wearing gloves or wiping off their fingerprints from any objects they touched.
The plethora of sources of information and tools available on the Internet make evidence hiding techniques, destruction methods, and spoofing more and more common. The poor implementation of logging solutions and the lack of SIEM continuous monitoring give often more space and time to a perpetrator to commit a crime and then time try to cover their tracks.
During a recent forensics assessment that aimed at ascertaining the details of a financial fraud incident, ProCheckUp identified that anti-forensics had been used in an attempt to eliminate incriminating evidence from a corporate laptop. The case involved a payment processing system (PPS), with unauthorised payments shy of half a million pounds. The employee’s PPS account credentials were used to put in unauthorised payments a couple of days before the cut-off date.
ProCheckUp looked at the employee’s corporate account activity on the corporate servers and a corporate laptop. The first objective was to forensically evaluate the data within the systems involved by examining related log-based data and file information in order to determine the extent of the employee’s involvement to the incident in question. The secondary objective was to identify evidence of external access to the system used for invoicing (as the event appears to have taken place out of hours).
The evaluation and analysis of the data for this case, including the laptop’s forensic analysis was performed on ProCheckUp’s secure digital forensics lab. A dedicated Digital Forensics consultant was assigned to the case. The device in question along with relevant evidence was collected in-person out-of-hours establishing a start point of chain of custody which was maintained until the end of this case. Server logs were also extracted, collated and later uploaded to the secure ProCheckUp portal. Log entries were correlated through timeline analysis to ascertain key events for this case.
It should be noted that ProCheckUp’s recommended standard Incident Response (IR) procedures (used as part of our IR Service), were not fully followed by our client. As a result, the remote server logs only captured limited information on remote access around the time of the incident. Key data such as the remote IP address was not captured in the logs (due to inadequate configuration of the logging system). Other network device logs (LAN) revealed that the user’s account of the employee in question, was logged in on the day of the event. Again, issues with the configuration of the Windows logging event system did not allow for discrete events which could help identify and pinpoint further information (as locking and unlocking of a system) to be captured.
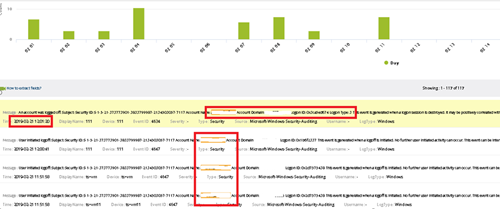
Figure 1: Log analysis sample identifying access to the system - During our investigation for this case ProCheckUp identified, analysed and correlated approximately more than 600000 recorded events a sample of which can be seen above.
ProCheckUp then focused the investigation on examining the laptop’s user space for files modified within the last 120 integrity, software installations, user account changes and related issues. As standard, once in the secure ProCheckUp’s lab the laptop based analysis conducted was focused on its PCI express M.2 disk. The disk’s encryption was bypassed, and the contents of the disk have been forensically analysed. ProCheckUp employs industry standard tools and techniques throughout handling, processing and assessing of any evidence provided or acquired.
Employees use corporate laptops that dock in docking stations provided on their desks. Once attached these act as normal desktops with access through the wired and wireless networks of a number of services. Simply powering up a device connected on a corporate network generates multiple events which can prove the presence of a device on the network.
It is worth mentioning that the financial fraud incident had taken place a few weeks earlier. The laptop in question was kept at the employee’s house for a few days following the incident before asked to surrender it. The employee in question claimed that their laptop had not been used for at least two months prior to the event.
ProCheckUp’s laptop findings validated that all data on the laptop pointed that the device had not been used for at least two months. However, it immediately became apparent that this did not match basic server logs entries for this device and observed employee activity at the premises. According to their line manager the employee in question has been continuously employed and coming to work until a few days after the incident.
The entries on the server logs identified key events for this case based on standard Windows network notification events that indicated that the employee laptop had been in use within the corporate network. However, the laptop contained files with timestamps and Operating System (OS) events pointing that the laptop was not used for two months prior to the incident. The payroll account used could not have been accessed by a malware due to the nature of the login process. In addition, two separate antivirus and antimalware solutions were in place. So that left only three logical options:
a) That a different device (laptop) was used when this employee went in to work;
b) That a different account was used when this employee accessed the corporate network;
c) That this device (laptop) was used but before it was surrendered, it was re-imaged with a Hard Disk image taken two months earlier to the incident.
Following discussion with our client, options a and b were quickly eliminated. Hard disk imaging is quite easy these days using hardware or software solutions and on a number of cases we have seen devices that have been re-imaged before are surrendered to erase incriminating evidence.

In conclusion anti-forensic tools, techniques and methods are becoming a formidable obstacle and a common practise employed by perpetrators. With the rise of cybercrime, as well as the amount of software which can be used to interfere with forensic investigations, Computer Forensic Investigations must be able to identify anti-forensic activity by using appropriate data correlation techniques.


Categories