GovAssure
Govassure serves as the cornerstone of the UK government's information assurance strategy, offering a standardised framework to assess and mitigate risks across various departments.
GovAssure: The Five Step Process
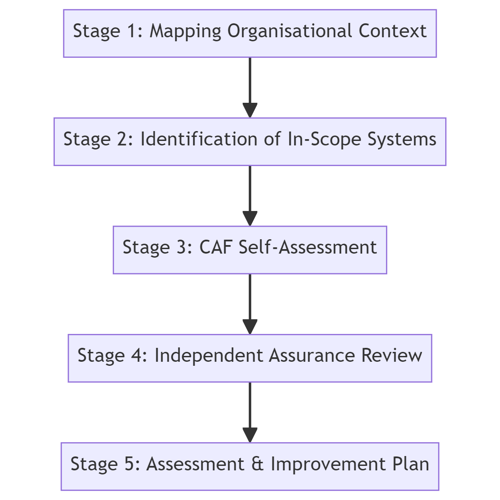
GovAssure is orchestrated through a methodical five-stage process designed to ascertain and uplift the cyber-security measures within an organisation..
Stage 1: Mapping Organisational Context for Essential Services
In this initial phase, the organisation embarks on a mission to discern its essential services. It's a strategic endeavor to comprehend the unique operational landscape, which is instrumental in shaping the scope of the GovAssure assessment. This tailored approach ensures that the review is both relevant and efficient. (Ownership: The Organisation)
Stage 2: Identification and Categorization of In-Scope Systems
During the second stage, the organisation's focus shifts to the critical systems that underpin the delivery of key services. It's about establishing clear system boundaries and assigning a CAF profile — either Baseline or Enhanced — in accordance with the system's significance and exposure to potential threats. This classification is pivotal in determining the intensity and nature of the assessment that follows.
(Joint Ownership: The Organisation and the Government Security Group)
Stage 3: Conducting a CAF Self-Assessment
Here, organisations engage in a comprehensive self-assessment against the backdrop of the CAF Guidance. The process includes a comparative analysis against other frameworks and assimilating evidence that epitomizes good practice — providing a reflective insight into the organization’s cyber-security stature.
(Joint Ownership: The Organsation and the Government Security Group)
Stage 4: Independent Assurance Review
An independent assurance review is paramount in validating the self-assessment. This stage is anchored by assessors who are not just neutral but also comply with the highest standards of security and assurance — injecting credibility into the process.
(Joint Ownership: Independent Assurance Reviewer, The Organisation, and the Government Security Group)
Stage 5: Comprehensive Assessment and Development of an Improvement Plan
The finale of the process is a comprehensive report that not only evaluates the organization’s cyber-security alignment with the CAF profile but also provides a directional blueprint for enhancement. It’s a cornerstone document for fostering informed investment decisions and driving strategic cyber-security initiatives. (Ownership: Independent Assurance Reviewer, The Department, and the Government Security Group)
For More Information Please Contact Us

ACCREDITATIONS






