What Are Code Reviews?
A code review involves examining the source code of computer software, serving not only to catch errors and ensure compliance with coding standards but also to facilitate knowledge sharing among developers. This collaborative exercise enhances the quality of software and bolsters the developers' understanding of the codebase. promoting a culture of continuous learning. Code reviews are one of the most important steps within the Software Development Life Cycle (SDLC) as they help to identify and rectify vulnerabilities and bugs, to ensure adherence with corporate coding standards.

Table of Contents
- What Are Code Reviews?
- What Is The Purpose Of A Code Review?
- What Are The Best Practices For Code Reviews?
- What Is The Code Review Process?
- What Technologies Power Modern Code Reviews?
- Comparing The Different Types of Code Review Technologies
- What Are The Industry Standards In Code Reviews?
- What Tools and Technologies Are Used In Code Reviews?
- What Are The Challenges and Solutions in Code Reviews?
- What Is The Future of Code Reviews?
- Integrating Code Review into the SDLC
- Common Questions
What Is The Purpose Of A Code Review?
Beyond quality assurance, code reviews are instrumental in cyber-security strategies. They enable early detection of vulnerabilities, compliance with security standards, and maintenance of high-quality, maintainable code. Regular reviews cultivate a security-aware culture among developers, ensuring software resilience against evolving cyber threats:-
- Early Detection of Vulnerabilities: By analysing each line of code potential security vulnerabilities can be. Resolved before deploying the software.
- Ensuring Compliance, with Security Standards: Code reviews play a role in ensuring that the software meets established security standards. Follows best practices thereby reducing the risk of security breaches.
- Ensuring Quality Assurance: In addition to security code reviews help maintain high quality code resulting in easily maintainable software.
- Promoting Developer Education: Regular code reviews foster a culture of awareness among developers about security practices.
- Safeguarding Software Integrity: It is important to ensure that the software remains secure and robust against evolving cyber threats.
What Are The Best Practices For Code Reviews?
To maximise the benefits of code reviews, define clear objectives for each session, involve a diverse review team, use standardised checklists, and keep sessions focused. :-
- Clearly Define Review Objectives: Establish goals for each review session such as focusing on identifying security vulnerabilities enforcing coding standards or assessing overall code quality.
- Include Appropriate Team Members: Involve a diverse group of individuals including developers, security experts and if possible an impartial third party reviewer to provide unbiased perspectives.
- Utilise a Standardised Checklist: Develop a checklist encompassing all aspects of security and quality that should be evaluated during the review process.
- Keep Reviews Focused and Time bound: Set limits, on the scope of each review session to prevent fatigue and ensure thoroughness.
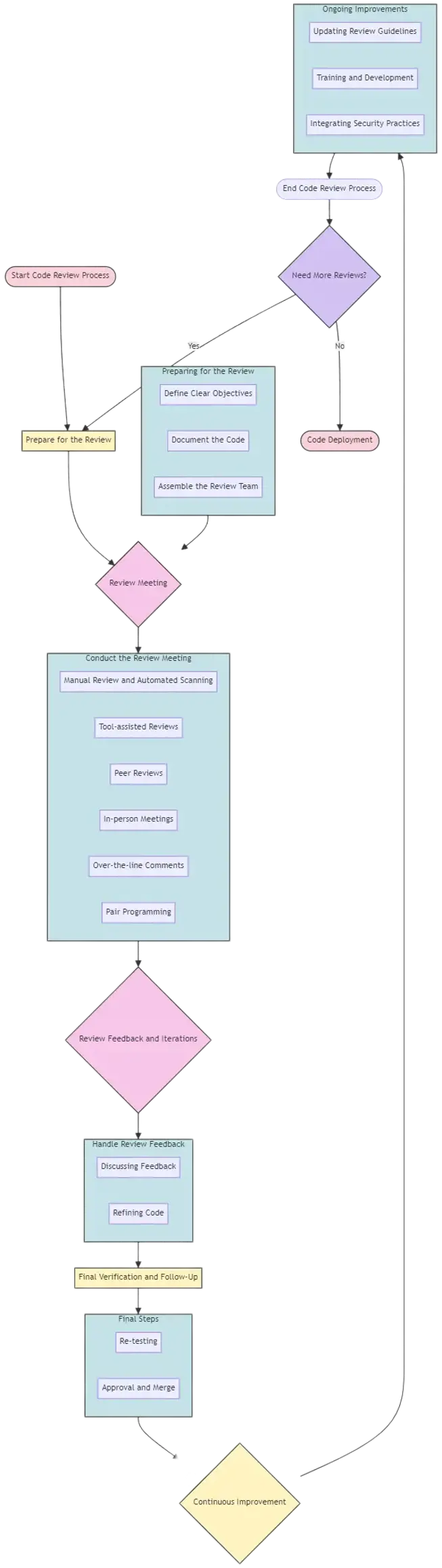
What Is The Code Review Process?
A well-structured code review process includes preparation, where code is documented and reviewers are briefed; a review meeting, utilising tools for tracking changes and comments; and post-review actions, where feedback is addressed to refine and secure the code further.

Preparing for the Review
Preparation is the first step in the code review process, where specific goals and standards for the review are established based on the project's requirements and security policies. Developers and reviewers gather relevant documentation, including requirement specifications, design documents, and coding standards. It's crucial that the reviewers have a good understanding of the code's purpose, functionality, and security implications. Preparation might also involve setting up a review schedule that aligns with project timelines and making sure all tools and systems are ready for the review process.
This includes:
- Defining Clear Objectives: Set specific, measurable objectives that align with your project’s security needs and regulatory compliance. This might include identifying security vulnerabilities such as SQL injections and cross-site scripting (XSS), ensuring the code adheres to the OWASP Top 10 security risks, or simply improving the code quality.
- Documenting the Code: Ensure that all code is well-documented and easy to understand. Documentation should include comments explaining the purpose of complex code segments and the functionality of various components within the application.
- Assembling the Review Team: Form a diverse group of reviewers that includes developers, security experts, and quality assurance personnel. Each member should bring a unique perspective and expertise to catch different types of potential issues.
The Review Meeting
Once preparation is complete, the actual review begins.During the review, the focus is on identifying any code that doesn't comply with the agreed-upon coding standards, as well as looking for logic errors, bugs, security vulnerabilities, and other issues. Reviewers comment on aspects such as code structure, maintainability, performance, and security practices. The goal is to ensure the code is efficient, understandable, maintainable, and secure.
This can be conducted in various formats:
- Manual Review and Automated Scanning: Use a combination of manual reviewing techniques and automated tools. Automated tools can scan for common vulnerabilities and coding errors quickly, while manual reviews provide deep insights into the business logic and more complex security vulnerabilities that automated tools might miss.
- Tool-assisted reviews: Utilising static code analysis tools to detect potential issues.
- Peer Reviews: Encourage peer reviews to foster a collaborative environment where knowledge and best practices are shared. This also helps in mentoring less experienced developers and enhancing their coding and security skills.
- In-person meetings: Where reviewers discuss the code together.
- Over-the-line comments: In source code management systems like GitHub or GitLab.
- Pair programming: Where two programmers work together at one workstation and continuously review the code as it's written.
Review Feedback and Iterations
Once the initial review is complete, the findings are compiled and shared with the original code authors:
- Discussing Feedback: Conduct meetings or discussions to go over the feedback. This helps in understanding the context and reasoning behind certain code segments and the associated feedback.
- Refining Code: Based on the feedback, developers refine the code to fix identified issues. This involves fixing reported issues, refactoring code, and possibly rewriting sections to improve clarity or performance.Priority should be given to critical vulnerabilities that pose the highest risk. The revised code is usually re-submitted for another round of review to ensure all concerns are addressed..
Final Verification and Follow-Up
After the necessary modifications are made, a final review is conducted to ensure all issues have been addressed:
- Re-testing: Re-test the updated sections of code to ensure that the changes have not introduced new issues and that all vulnerabilities have been adequately addressed.
- Approval and Merge: Once the final verification is complete, the code can be approved for merging into the main codebase.
This phase includes actions to integrate the improved code back into the project's codebase. This involves merging the changes, updating task tracking systems, and sometimes conducting regression tests to ensure the new code does not adversely affect existing functionality. Documentation may also be updated to reflect any significant changes or decisions made during the review process.
Continuous Improvement
The code review process is iterative and should evolve based on new insights and industry best practices:
- Updating Review Guidelines: Regularly update the code review guidelines to incorporate new security threats, technological advancements, and industry standards.
- Training and Development: Continuously train the development team on the latest coding and security practices to improve their skills and awareness of potential security issues.
Security Integration:
Integrating security throughout the code review process ensures a proactive approach to software development.
This includes:
- Utilising Security Tools: Implement tools that perform Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and other relevant security checks.
- Vulnerability Tracking: Keep track of identified vulnerabilities and ensure they are addressed before the software goes into production.
What Technologies Power Modern Code Reviews?
Technologies like Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) play crucial roles, alongside newer methodologies like Interactive Application Security Testing (IAST) and Runtime Application Self-Protection (RASP), enhance the precision and scope of security assessments.
Static Application Security Testing (SAST)

Static Application Security Testing (SAST) plays a role in the code review process. SAST involves analysing source code or compiled versions of code to identify security vulnerabilities without executing the program. It is a method for detecting flaws on during software development, which helps reduce the risk of security breaches after deployment.
Key Features of SAST:
- Early Detection of Vulnerabilities: SAST tools scan the code. Identify vulnerabilities at the stages of development even before running the code.
- Comprehensive Code Coverage: These tools analyse the code base providing a review of all application components.
- Automated Scanning: SAST offers automated scanning capabilities making it easier to integrate into continuous integration/continuous deployment (CI/CD) pipelines.
- Language Specific Analysis: SAST tools are often designed for specific programming languages providing detailed analysis based on language specific syntax and semantics.
Industry Application:
SAST is widely utilized in industries where security holds importance, such, as finance, healthcare and government sectors.
Dynamic Application Security Testing (DAST)

Dynamic Application Security Testing (DAST) involves an automated process that tests web applications while they are running to identify any security vulnerabilities that may arise during operation. Unlike SAST testing DAST takes on the perspective of an attacker by interacting with the application. This approach is crucial in detecting issues such as SQL injection, cross site scripting (XSS) and other vulnerabilities that become evident when the application is active. By incorporating DAST into the code review process organisations can ensure that their applications are not functionally robust but also shielded from threats.
Key Features of DAST:
- Real Time Analysis: DAST tools evaluate applications in their environment offering insights into real world security vulnerabilities.
- External Attack Simulation: These tools simulate attacks to provide a view of potential security breaches.
- Comprehensive Reporting: DAST generates reports on identified vulnerabilities, including information about their severity and potential impact.
- User Friendly Interface: Designed with accessibility, in mind DAST tools can be effectively utilized by professionals without knowledge of the applications source code.
Industry Application:
DAST is widely utilised in industries where ensuring web application security is of importance such, as e commerce, banking and healthcare. It proves to be highly valuable in scenarios where applications experience updates and changes necessitating ongoing security assessments. The fact that DAST can test applications while they are operational makes it a preferred choice for organizations that prioritize real time security assurance.
Interactive Application Security Testing (IAST)

Interactive Application Security Testing (IAST) is an approach in the field of code reviews combining elements from both Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). IAST tools function within the application itself continuously analysing the code as the application runs. This methodology offers a perspective by providing the accuracy of analysis along with practical insights derived from dynamic testing. IAST excels at identifying security vulnerabilities that're contextually relevant to an applications operational environment.
Key Features of IAST:
- Real Time Code Analysis: IAST tools analyze the source code of an application while it is being executed delivering feedback, on any security issues.
- Combination of SAST and DAST: By merging aspects from both SAST and DAST IAST provides an overview of an applications security status.
- Minimal False Positives:The analysis conducted by IAST yields instances of positives compared to other testing methods. One advantage of IAST tools is their integration, into the software development life cycle making them a developer friendly choice for security assessment.
Industry Application:
In industries such as services, healthcare and e commerce IAST holds significant value due to its ability to ensure software security. It excels in development environments and DevOps practices where real time feedback is crucial for iteration and continuous deployment.
Runtime Application Self-Protection (RASP)
Another noteworthy security technology is Runtime Application Self Protection (RASP) which integrates with applications to control execution detect and prevent attacks in time. Unlike code reviews that may overlook vulnerabilities RASP operates within the application itself. Provides continuous monitoring and protection during runtime.
Key Features of RASP:
- Real Time Threat Detection: RASP promptly. Blocks threats as they happen, without requiring intervention.
- Context Aware Protection: When using the application RASP has the ability to understand the context, which helps it make decisions, about what is considered normal behavior and what could be an attack.
- Minimal Performance Impact: RASP is designed to run ensuring that it does not have an impact on the performance of the application.
- Customisable Security Policies: You can customize security policies with RASP to meet the needs of your application.
Industry Application of RASP
- Financial Services: RASP protects transactions and customer data from real time threats.
- Healthcare: RASP ensures the security and privacy of healthcare applications keeping data safe.
- E commerce: RASP shields e commerce platforms from attacks like SQL injection and cross site scripting.
Software Composition Analysis (SCA)

Software Composition Analysis (SCA) is an approach that involves identifying and evaluating open source components used in a software application. SCA tools scan an applications source code, binaries or byte code to detect open source libraries, frameworks and other components. These tools assess them for security vulnerabilities, licensing issues and quality metrics. This analysis is vital, in today's software development landscape where open source components are widely used but can pose security risks or licence and copyright issues if not managed properly.
Key Features of SCA:
- Detecting Vulnerabilities: SCA tools can identify known vulnerabilities, in open source components used within applications.
- Ensuring License Compliance: These tools assess open source licenses to help organizations adhere to requirements.
- Automated Alerts: SCA provides alerts for discovered vulnerabilities enabling timely responses.
- Dependency Tracking: It tracks dependencies and sub dependencies within open source components to understand the scope of risks.
Industry Application of SCA
- Technology Sector: SCA ensures that software products in tech companies are secure and comply with open source licenses.
- Financial Services: It helps manage risks associated with open source components in financial software systems.
- Healthcare Industry: SCA assists in maintaining the security and compliance of healthcare applications those handling patient data.
Comparing The Different Types of Code Review Technologies
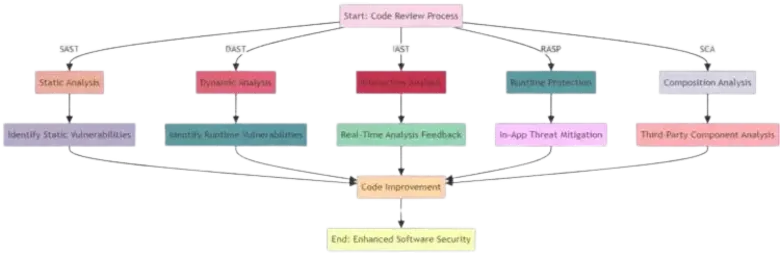
Static Application Security Testing (SAST):
- Overview: SAST tools analyse source code to identify vulnerabilities without executing the program.
- Advantages: Early detection of vulnerabilities; integration into the development process; identification of complex security issues.
- Drawbacks: Potential for false positives; limited in identifying runtime vulnerabilities; requires expert interpretation.
Dynamic Application Security Testing (DAST):
- Overview: DAST involves testing an application during runtime to find vulnerabilities that are exploitable.
- Advantages: Identifies vulnerabilities in a running application; simulates real-world attack scenarios; tests application in its operational environment.
- Drawbacks: Limited to detecting vulnerabilities exposed during runtime; cannot identify source code issues.
Interactive Application Security Testing (IAST):
- Overview: IAST combines elements of SAST and DAST, providing real-time security analysis of applications from within.
- Advantages: Accurate detection by combining static and dynamic analysis; immediate feedback; broad vulnerability coverage.
- Drawbacks: Requires application to be in a running state; potentially complex integration.
Runtime Application Self-Protection (RASP):
- Overview: RASP integrates with an application to provide real-time threat detection and response.
- Advantages: Protects applications during runtime; immediate threat mitigation; enhanced application self-awareness.
- Drawbacks: Potential performance impact; limited to the application it is integrated with.
Software Composition Analysis (SCA):
- Overview: SCA tools analyze open-source components within applications for known vulnerabilities.
- Advantages: Identifies vulnerabilities in third-party components; ensures compliance with open-source licenses.
- Drawbacks: Reliant on vulnerability databases; may not cover proprietary code.
What Are The Industry Standards In Code Reviews?
In the field of cyber-security following industry standards during code reviews is essential to ensure the security and reliability of software. These standards offer guidelines and best practices to identify and mitigate security vulnerabilities in code. They are developed by cyber-security experts. Are continuously updated to address emerging threats and advancements in technology.
-
OWASP Secure Coding Practices: These guidelines serve as a framework for coding assisting developers in preventing security vulnerabilities.
-
ISO 27001;2022 Annex A Control 8.28: This control aids organizations in mitigating security risks and vulnerabilities that may result from software coding practices by establishing, implementing and reviewing secure software coding practices.
-
NIST Special Publications: The National Institute of Standards and Technology (NIST) provides a range of publications that offer guidance and best practices for information security. These publications are widely respected and utilized by organizations to guide their cybersecurity efforts, including code reviews.
What Tools and Technologies Are Used In Code Reviews?
This section explores the tools and technologies used for a code review, that play a role in effective code reviews explaining their functions, advantages and how they fit into the software development life cycle.

Static Application Security Testing (SAST) Tools:
- Summary: SAST tools analyse source code to identify vulnerabilities without executing the program. They are important for detection of security flaws during the development process.
- Popular Tools: Some examples of used SAST tools are SonarQube, Fortify and Checkmarx.
- Integration in Development: SAST tools are often integrated into Integrated Development Environments (IDEs) and Continuous Integration/Continuous Deployment (CI/CD) pipelines to ensure security assessment.
Dynamic Application Security Testing (DAST) Tools:
- Summary: DAST tools test applications while they are running by simulating attacks to uncover vulnerabilities at runtime.
- Popular Tools: OWASP ZAP, Burp Suite and Acunetix are among the used DAST tools.
- Usage: These tools are typically employed during stages of development and in Quality Assurance (QA) testing environments.
Code Review Platforms:
- Summary: Platforms like GitHub, GitLab and Bitbucket offer code review capabilities that enable developers to review and discuss code.
- Features: These platforms provide features such as requests, inline comments and integration with issue tracking systems.
Peer Review Tools:
- Overview: Tools like Crucible and Review Board facilitate peer reviews enabling teams to examine each others code for quality and security.
- Benefits: Peer reviews promote knowledge sharing. Enhance code quality through collective expertise.
Integrated Development Environments (IDEs):
- Overview: Many IDEs have integrated tools for code analysis and review.
What Are The Challenges and Solutions in Code Reviews?
Code reviews are a integral part of the software development process. They ensure that the code is not only functional but is also secure and efficient. However there are challenges that can affect their effectiveness. It is crucial to understand these challenges and implement solutions to optimize the code review process.
Time Constraints:
- Description: Code reviews can be time consuming often causing project delays.
- Solution: Utilize automated tools, for routine checks so that human reviewers can focus on more complex issues.
Review Quality:
- Description: The effectiveness of a code review greatly relies on the expertise and experience of the individual conducting it.
- Solution: Implement training programs and continuous learning opportunities for developers to enhance their skills in conducting reviews.
Consistency:
- Description: Ensuring consistency in code reviews when different individuals are involved can pose challenges.
- Solution: Establish checklists and guidelines for code reviews to promote uniformity.
Collaboration and Communication:
- Description: Effective communication among team members is crucial but often presents difficulties.
- Solution: Utilize tools and platforms that facilitate clear and seamless communication.
Handling Feedback:
- Description: Negative feedback can occasionally lead to demotivation or conflicts.
- Solution: Cultivate a culture where feedback is constructive emphasizing learning and growth
What Is The Future of Code Reviews?
The realm of code review, in cyber security is rapidly evolving, driven by advancements and the ever changing landscape of cyber threats. Looking ahead there are significant trends and innovations that will redefine how code reviews are conducted making them more efficient, effective and an integral part of the software development life cycle.

AI and Machine Learning Integration:
- Description: The integration of Artificial Intelligence (AI) and Machine Learning (ML) into code review tools is becoming more common, automating and enhancing the detection of vulnerabilities.
- Impact: This integration will result in accurate and efficient reviews saving time and resources while improving the overall quality of the analysis.
Increased Emphasis on DevSecOps:
- Description: DevSecOps, which involves integrating security into every phase of software development is gaining prominence.
- Impact: This approach ensures that security considerations are not overlooked but rather an integral part of development leading to secure software.
Enhanced Focus on Secure Coding Education:
- Description:There is a growing recognition of the importance of educating developers in secure coding practices.
- Impact: By providing developers with the knowledge and tools to write secure code there will be less reliance on post development code reviews.

Expansion of Code Review to Emerging Technologies:
- Description: With the rise in prominence of emerging technologies such as IoT and blockchain code review processes must adapt to these paradigms.
- Impact: This expansion necessitates the development of tools and methodologies to address unique security challenges presented by these technologies.
Integrating Code Review into the Software Development Lifecycle (SDLC)
Integrating code review into the Software Development Life-cycle (SDLC) is an approach that enhances the security and quality of software products. This integration ensures that code review is not a standalone activity but an ongoing and essential part of the entire development process.
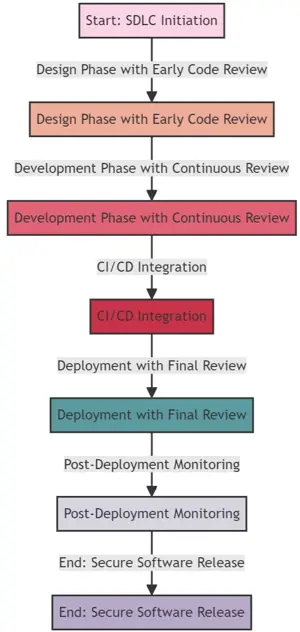
Early Integration:
- Explanation: Including code review in the SDLC ideally during the design and development stages.
- Advantages: Early identification of vulnerabilities resulting in reduced costs and effort to fix issues later on.
Automated and Manual Reviews:
- Explanation: Combining automated tools with expertise for a comprehensive review process.
- Advantages: Automation accelerates the review process while human reviews provide depth and context to the findings.
Continuous Integration and Continuous Deployment (CI/CD):
- Explanation: Integrating code review into CI/CD pipelines for security checks.
- Advantages: Ensures continuous security assurance and enables quick feedback loops.
Collaboration and Knowledge Sharing:
- Explanation: Promoting collaborative reviews and knowledge sharing among developers.
- Advantages: Cultivates a culture of learning and continuous improvement, in coding practices.
Feedback and Iteration:
- Explanation: Gathering feedback and insights after deployment monitoring to iterate on development cycles for improvement.The Impact phase is crucial as it allows us to apply the lessons learned from the cycle to future projects.
- Advantages: This ongoing process continuously enhances the security and quality of our software.
Regular Updates and Maintenance:
- Explanation: It is essential to regularly update and maintain the software in order to address newly discovered vulnerabilities and meet changing requirements.
- Advantages: By doing so ensures that the software remains secure and functional over time adapting effectively to new threats and user needs.
Continuous Learning and Adaptation:
- Explanation: Emphasize the importance of continuous learning and adaptation, in the fields of cyber security and software development.
- Advantages: This approach ensures that the development team(s) stays updated with the security trends and technologies fostering a culture of continuous improvement.
Common Questions
A code review is a critical practice within software development aimed at improving the security and quality of code. Below are some commonly asked questions to provide clarity on its purpose and how it is executed..
1. What is Code Review in Software Development?
Answer: A code review is the systematic examination of computer source code. It aims to find and fix errors overlooked during initial development, improve overall software quality, and enhance the developers' skills by facilitating knowledge sharing.
2. How Does Code Review Differ from Software Testing?
Answer: While software testing involves executing code to find bugs or performance issues, code review is a preemptive practice that focuses on analyzing the written code to identify errors or bad practices before the software is run. It helps to catch issues that testing may not detect.
3. What are the Benefits of Conducting Code Reviews?
Answer: Code reviews improve software quality by catching bugs early, ensuring compliance with coding standards, reducing future maintenance costs, enhancing security, and fostering a collaborative culture that promotes knowledge sharing among developers.
4. Who Should Participate in a Code Review?
Answer: Code reviews should ideally include multiple developers, not just the author of the code. Including peers, senior developers, and occasionally, security experts can provide diverse insights and more comprehensive feedback.
5. What are the Best Practices for Conducting Effective Code Reviews?
Answer: Effective code reviews involve clear objectives, a diverse review team, the use of checklists, focused sessions, and constructive feedback. Using tools to facilitate the review process and maintaining a positive and educational approach are also crucial.
6. How Often Should Code Reviews Be Conducted?
Answer: The frequency of code reviews can vary based on the project's complexity and the organization's development methodology. In agile environments, reviews may be integrated into the regular sprint cycles to ensure continuous improvement.
7. What are the Ethical Considerations in Code Review?
Answer: Ethical considerations include ensuring confidentiality of the code, providing respectful and constructive feedback, maintaining professionalism, and fostering an inclusive environment where all participants feel valued and heard..
For More Information Please Contact Us

ACCREDITATIONS






