In the dynamic landscape of cyber-security, pushing the boundaries of traditional testing methodologies is essential. This blog post discusses a recent IVR system test conducted by the ProCheckUp team, shedding light on its unique approach and methodologies used, the uncovered vulnerabilities, and the transformative impact of such innovation on the security of IVR systems.
What are Interactive Voice Response systems?
Interactive Voice Response (IVR) systems are automated telephony systems that interact with callers through voice and touch-tone keypad inputs. They play a crucial role in customer service by providing a structured and interactive interface for users to obtain information, perform transactions, or navigate through various options. IVR systems are commonly used in sectors such as banking, healthcare, telecommunications, and customer support.
IVR systems often manage sensitive information such as personal identification numbers (PINs), account details, and other confidential data. Penetration testing helps assess the security posture of an IVR system, identifying vulnerabilities and weaknesses that could be exploited by malicious actors.
Recognising a gap in available resources for IVR system penetration testing, the ProCheckUp team set out to bridge the gap in IVR security testing, ensuring these systems are fortified against advanced threats.
The ProCheckUp Approach to IVR Testing

Before any sort of testing could begin, a meticulous process of mapping out each aspect of the target IVR system was needed. This involved a comprehensive exploration of every workflow within the system, to identify potential vulnerabilities and any entry points that might be susceptible to exploitation. The ProCheckUp team engaged in a detailed analysis to understand how these entry points could be targeted, examining the system's architecture and intricacies to uncover weak links.
The initial phase involved unravelling the intricacies of IVR workflows, pinpointing critical junctures where vulnerabilities might lurk. Identifying potential entry points was a strategic endeavour, requiring a nuanced understanding of the system's structure and functionality. Once these entry points were recognised, the focus shifted to devising attack strategies tailored to exploit the specific vulnerabilities associated with each one.
This meticulous mapping process laid the foundation for the subsequent creation of bespoke scripts, simulating real world cyber attacks against IVR systems. By thoroughly understanding the IVR system's workflows, vulnerabilities, and potential points of exploitation, we were able to craft bespoke scripts that simulated real-world attack scenarios. This approach ensured that the penetration testing efforts were not only comprehensive but also precisely aligned with the unique challenges posed by the IVR systems under scrutiny.
Crafting Bespoke Scripts

Addressing the scarcity of testing scripts for IVR testing, the team developed bespoke scripts to simulate denial-of-service (DoS) attacks using the Twilio API. This approach not only highlights our commitment to advancing cybersecurity testing but also provides a blueprint for future security research.
See below the bespoke Twilio script created for account number enumeration:-
|
|
This Python script sets up a web application integrated with Twilio to create an Interactive Voice Response (IVR) system. The application oversees incoming speech input from a phone call, generating dynamic responses based on the detected keyword "security." If the user mentions "security," the script generates a random 8-digit account number and marks it as either valid or invalid. The script then initiates another phone call and plays a TwiML response with a pause, playing the digit "5," followed by the generated account number. The script continuously runs in a loop, making periodic calls, and logging the generated account numbers in a file named 'valid_accounts.txt.' The entire process responds in an interactive and dynamic manner, responding differently based on the detected speech input.
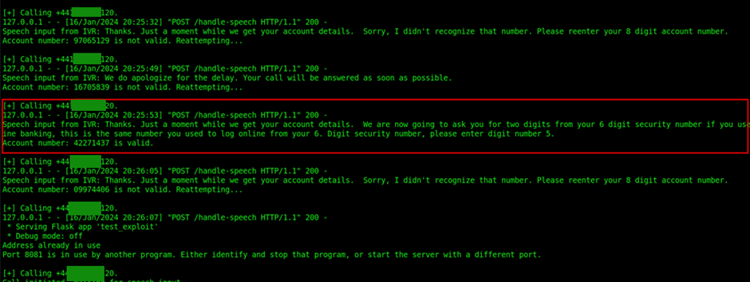
Figure 1: bespoke Script running, showing an account number being successfully found
Several bespoke scripts were meticulously developed to scrutinise various workflows within the IVR system. These scripts systematically assessed the susceptibility of the IVR systems to potential security threats, including but not limited to malicious payloads, special characters, and other attacks. Specifically, the evaluation involved a thorough examination of special character inputs and malicious payloads during IVR interactions.
Revealing IVR Vulnerabilities:

Denial-of-Service Vulnerabilities Exposed:
The testing revealed critical vulnerabilities within the IVR system, including the lack of call rate limiting for specific numbers and insufficient account lockout policies to defend against potential account number DoS attacks.
The absence of call rate limiting poses a significant threat to the availability of the telecommunications service. Without proper rate limiting, malicious actors could exploit this vulnerability to flood the system with a large number of calls, leading to a potential denial-of-service (DoS) scenario. The sheer volume of calls could overwhelm the telecommunication infrastructure, causing service degradation or complete unavailability for legitimate users.
In a controlled test, our team deployed a bespoke script to systematically place over three hundred calls to a targeted voice number within our testing scope. Remarkably, these calls proceeded without any imposed restrictions or errors, starkly highlighting the absence of essential controls needed to regulate the frequency of incoming calls to a voice number.
Enumeration Risks: Account and Credit Card Numbers:
The exploration exposed vulnerabilities to enumeration of account and credit card numbers, underlining the importance of stringent input validation mechanisms for enhanced system security.
ProCheckUp discovered the possibility of account number enumeration on one of the IVR platforms. Specifically, if a user inputs the correct account number when prompted, they are subsequently prompted to enter their date of birth. In the event of an incorrect account number entry, users are presented with the option to re-enter the information or are seamlessly transferred to a customer service representative. The implementation of a new step following the correct entry of an account number serves as a validation mechanism.
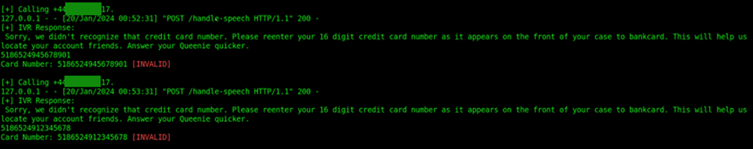
Similarly, the assessment revealed a potential vulnerability related to credit card number enumeration within a separate workflow. When users input the correct 16-digit credit card number, they are directed to the next menu. However, in the case of an incorrect entry, users are afforded an opportunity to retype the sixteen digits or are smoothly transferred to a customer service representative. Again, the implementation of a new step following the correct entry of long card number serves as a validation mechanism.
Testing for Social Engineering Vulnerabilities
Although this test did not have need for Red Teaming there are other vulnerabilities in the IVR system that are at risk. Malicious actors may attempt to manipulate IVR operators into providing sensitive information through social engineering. Read Teaming assesses the system's resistance to social engineering attacks, helping organisations fortify against deceptive tactics.
Strategies for Enhancing IVR Security

To mitigate these risks, we recommend a multifaceted approach is undertaken, including the implementation of account lockout policies, rate limiting, randomized response mechanisms, and multi-factor authentication. These strategies are essential for safeguarding IVR systems against both brute-force attacks and sophisticated social engineering tactics.
Exploring the significance of addressing IVR vulnerabilities reveals that securing these systems is not merely about protecting user data but is a pivotal element in strengthening an organisation's holistic cybersecurity stance. Below, we provide remediation tips aimed at minimising the risks associated with IVR systems.
Implement Account Lockout Policy:
Introduce an account lockout policy that temporarily locks user accounts after a certain number of failed attempts. This helps prevent attackers from systematically enumerating account numbers through brute-force attacks.
Rate Limiting and Monitoring:
Implement rate limiting on the IVR system to restrict the number of attempts a user can make within a specified time frame. Monitor system logs for patterns indicative of enumeration attacks and set up alerts for suspicious activities.
Randomised Responses:
Configure the IVR system to provide randomised responses for invalid account number entries. This can make it more challenging for attackers to determine valid account numbers through automated enumeration techniques.
Enhanced Authentication Measures:
Strengthen the authentication mechanisms for accessing the IVR system. Consider implementing multi-factor authentication to add an extra layer of security and reduce the risk of unauthorised access.
Secure Communication Channels:
Ensure that communication channels between the IVR system and other components are secure. Use encryption protocols to protect sensitive data, including account numbers, during transmission.
Regular Security Assessments:
Schedule regular security assessments, including penetration testing, to identify and address vulnerabilities in the IVR system proactively. Engage with security professionals to perform thorough testing and provide insights into potential weaknesses.
User Education and Awareness:
Educate users and administrators about the risks associated with account information enumeration. Encourage the reporting of any suspicious activities and emphasise the importance of following secure practices.
Compliance with Security Standards:
Ensure that the IVR system aligns with industry-specific security standards, such as the Payment Card Industry Data Security Standard (PCI DSS) or any other applicable regulations. Compliance with these standards provides a baseline for securing sensitive information.
Incorporate Delay Mechanisms:
Introduce delays or timeouts between unsuccessful login attempts to slow down automated enumeration attacks. This can make it more time-consuming and less feasible for attackers to perform large-scale enumeration.
Regularly Update and Patch:
Keep the IVR system and its components up-to-date with the latest security patches and updates. Regularly check for vendor-supplied patches and apply them promptly to address any known vulnerabilities.
Conclusion

In conclusion, the exploration into IVR system vulnerabilities conducted by the ProCheckUp team has not only revealed critical security gaps but has also showcased our innovative approach to penetration testing. The use of bespoke scripts, such as those simulating denial-of-service attacks, demonstrated the team's commitment to pushing the boundaries of traditional testing methodologies in the ever-evolving landscape of cybersecurity.
The vulnerabilities we’ve uncovered, particularly in the areas of denial-of-service risks, account and credit card number enumeration, emphasises the importance of robust security measures for IVR systems. The absence of call rate limiting and account lockout policies, and the potential exposure of sensitive information underscore the need for immediate attention to secure these critical systems.
Furthermore, our testing methodology not only focused on technical aspects but also considered social engineering vulnerabilities that could be exploited by malicious actors. This holistic approach aligns with the evolving nature of cybersecurity threats and reflects an initiative-taking stance toward fortifying organisations against deceptive tactics.
Our recommendations provide for minimising IVR vulnerabilities and risks serve as a comprehensive guide for organisations looking to enhance the security of their IVR systems. Implementing account lockout policies, rate limiting, randomised responses, enhanced authentication measures, secure communication channels, and compliance with industry standards are crucial steps toward building a robust defence against potential attacks.
The ProCheckUp team's findings and recommendations underscore the necessity for ongoing vigilance, regular assessments, and an initiative-taking security stance to safeguard IVR systems. As organisations implement these remediation measures, they contribute not only to the protection of sensitive information but also to the overall resilience of their cybersecurity infrastructure. The transformative impact of such innovation on the cybersecurity landscape is evident, reinforcing the importance of staying ahead in the constant battle against emerging threats.




Categories