The financial services sector is under constant threat from cyber-criminals, with attacks ranging from data breaches, financial fraud to denial of service attacks that target the availability of their Internet presence, financial firms have to comply with a series of robust cyber-security regulations designed to strengthen them against such threats. These regulations demand not only strict compliance but also provide a proactive stance on cyber-security, ensuring the protection of the critical financial infrastructure and sensitive customer data.
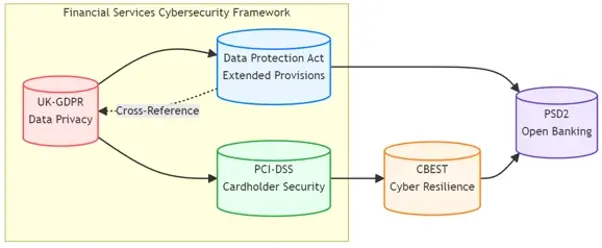
Financial Institution Cyber Regulations
UK-GDPR: Prioritising Data Privacy in Finance
The UK's General Data Protection Regulation (UK-GDPR) prioritises the safeguarding of personal data within the financial sector, aligning with European standards whilst acknowledging the nuances of the UK's legal framework following Brexit. Here's an overview of the recent developments and key aspects of the UK-GDPR as it stands today.

Recent Developments:
On the 28 June 2021, the European Commission adopted adequacy decisions for the UK under the EU’s General Data Protection Regulation (EU GDPR) and the Law Enforcement Directive (LED). These decisions recognise that the UK maintains an adequate level of data protection, comparable to that of the EU. This recognition allows for the continued free flow of personal data from the EU and EEA to the UK without additional safeguards, with the exception of data transferred for immigration control purposes. These adequacy decisions are scheduled for review by 2025, with a possibility of renewal for up to four more years.
Implementation Phases:
The adequacy decisions have established a stable foundation for UK businesses and organizations handling EEA data:
- Initial Recognition: Effective from 28 June 2021, acknowledging the UK's adequate level of data protection.
- Review Period: Set until 27 June 2025, after which the decisions may be extended, amended, or revoked based on ongoing assessments.
Components of UK-GDPR:
- Strong Customer Authentication and Secure Communications: UK-GDPR continues to enforce robust measures for data protection, including strong customer authentication requirements.
- Data Transfer and Management: Specific rules govern the transfer of personal data, especially regarding immigration control and other sensitive areas.
- Regulatory Oversight: The Information Commissioner's Office (ICO) remains the supervisory authority within the UK, providing guidance and enforcing data protection laws.
Objectives and Impact:
- Enhanced Data Protection: The UK-GDPR aims to protect personal data with standards essentially equivalent to those under the EU GDPR.
- Continued Data Flow: The recognition of the UK's adequacy facilitates uninterrupted data exchanges between the UK and EEA, crucial for economic relations and individual rights protection.
- Adaptation and Compliance: UK organisations must continuously adapt to the evolving landscape of data protection, ensuring compliance with both UK-GDPR and EU GDPR where applicable.
PCI-DSS: Securing Cardholder Data
The Payment Card Industry Data Security Standard (PCI-DSS) sets the bar for protecting cardholder information during and after cardholder transactions. Given the volume of credit and debit card use in financial services, compliance with PCI-DSS is not only mandatory but critical to maintaining consumer trust and avoiding the reputational damage that comes with data breaches.

Recent Developments:
The Payment Card Industry Data Security Standard (PCI DSS) has undergone significant updates with the release of Version 4.0 in March 2022. These updates ensure that the standards not only meet current security threats but also offer flexibility and support for additional methodologies to comply with the requirements. The introduction of a Customised Approach alongside the traditional Defined Approach allows organisations to tailor specific security measures that best fit their operational models while still achieving compliance.
Implementation Phases:
PCI DSS Version 4.0 implementation allows entities a transition period, recognising the need for organisations to adapt to the new requirements gradually. The phased approach helps entities plan and implement changes without compromising the security of cardholder data environments. The transition from Version 3.2.1 to Version 4.0 involves detailed timelines that organizations must follow to stay compliant, ensuring they understand and can execute new and evolving security demands effectively.
Components of PCI DSS:
The PCI DSS framework is structured around six major goals encompassing 12 key requirements. These include maintaining a secure network and systems, protecting cardholder data, maintaining a vulnerability management program, implementing strong access control measures, regularly monitoring and testing networks, and maintaining an information security policy. Each requirement is supported by specific sub-requirements and testing procedures to guide compliance. Version 4.0 enhances the scope of these components to include additional security practices for encryption, service providers, and the integration of new technologies.
Objectives and Impact:
The primary objective of PCI DSS is to protect cardholder data from breaches and theft. Compliance with PCI DSS not only helps in mitigating risks associated with security breaches but also aids in building trust with customers by demonstrating commitment to security. The impact of implementing PCI DSS standards is profound, offering a structured approach to security that aligns with best practices and international regulations. This compliance ensures that all participating entities, from merchants to service providers, uphold the integrity and confidentiality of cardholder data across transactions and storage environments.
Data Protection Act 2018
The Data Protection Act 2018 providing a framework that's specifically tailored to the UK context. Financial services must align with its provisions for processing personal data, with a particular focus on areas such as data subject rights, data protection impact assessments, and data sharing across borders.

Recent Developments:
The Data Protection Act 2018 has undergone several modifications and applications since its enactment. Notably, it was also affected by The Channel Tunnel (Arrangements with the Kingdom of the Netherlands) Order 2020, which applied and excluded certain parts of the Act. The Act has seen applications in various contexts, including changes post-Brexit with the substitution of EU references to UK specifics, highlighting its dynamic and adaptable framework to address the evolving data protection landscape.
Implementation Phases:
Since its enactment in 2018, the implementation of the Data Protection Act has been phased to allow organisations to adjust to new requirements gradually. These phases include the initial introduction of GDPR-aligned rules, followed by more detailed regulations such as those concerning law enforcement and intelligence services processing. Each phase aims to enhance personal data protection without disrupting existing operational capabilities critically.
Components of Data Protection Act 2018:
- General Provisions: Establishes the scope and definitions relevant to the entire Act. Most processing of personal data falls under the UK GDPR, supplemented by this Act.
- Law Enforcement Processing: Details data processing by competent authorities for law enforcement purposes, ensuring alignment with necessary legal standards.
- Intelligence Services Processing: Governs data handling by intelligence agencies, placing specific conditions and safeguards.
- Information Commissioner’s Role: Outlines duties and powers of the Information Commissioner as the supervisory authority for data protection in the UK.
- Data Subject Rights: Enumerates the rights of individuals concerning their personal data, including access, correction, and consent mechanisms.
- Regulatory and Compliance Frameworks: Specifies the obligations for data processors and controllers, including conditions for lawful processing and transfer of data.
Objectives and Impact:
The primary objective of the Data Protection Act 2018 is to provide a comprehensive legal framework for the protection of personal data across various sectors, including public administration, healthcare, and law enforcement. This Act aims to enhance individual rights and ensure high standards of data protection. It also aims to bolster public trust through stringent compliance requirements for data handlers.
The impact of this legislation has been significant, influencing how organisations manage data protection and compliance. It has also increased the accountability of data processors and controllers, reinforcing the importance of protecting personal data in a digital age. The Act supports the UK's ability to trade and exchange data with international partners by ensuring that its standards are compatible with international expectations, particularly in alignment with the GDPR standards.
CBEST: Strengthening Cyber Resilience
CBEST is a framework designed to improve the cyber resilience of the UK financial system. It involves rigorous testing and analysis of financial institutions' critical systems to assess their vulnerability to cyber-attacks. Compliance with CBEST standards means not just ticking regulatory boxes but ensuring that the very infrastructure of financial services can withstand sophisticated and persistent cyber threats.

The Financial Conduct Authority (FCA)
The FCA's regulations focus on protecting consumers, ensuring the integrity of the financial industry, and promoting healthy competition between financial services providers. Cyber resilience is a key part of the FCA's mandate, with guidelines for firms to identify vulnerabilities and to report cyber incidents to the Financial Conduct Authority by following the NCSC guidelines.

Senior Managers and Certification Regime (SMCR)
The Senior Managers and Certification Regime (SM&CR) was introduced to increase accountability in the financial services sector, enhance market integrity, and protect consumers. Established in response to the 2008 financial crisis and ensuing scandals like LIBOR manipulation, the regime focuses on ensuring individuals are accountable for their conduct and competence.

Implementation Phases:
- 2016: Initially applied to banks, building societies, credit unions, and PRA-designated investment firms.
- December 2018: Extended to include insurers.
- 2019: Broadened to cover all solo-regulated firms, excluding benchmark administrators.
- December 2020: Benchmark administrators were included under the regime.
- Recent Developments:
December 2022: HM Treasury announced a review of the SM&CR, leading to a 2023 call for evidence and concurrent reviews by the Financial Conduct Authority (FCA) and the Prudential Regulation Authority (PRA).
Components of the SMCR:
- Senior Managers Regime: Focuses on high-level accountability.
- Certification Regime: Requires firms to certify the suitability of staff in roles that could significantly harm the firm or its customers.
- Conduct Rules: Applies basic standards of behavior expected of all employees within regulated firms.
Objectives and Impact:
- Encourage individual responsibility and improve overall conduct within firms.
- Ensure clear understanding and delineation of roles and responsibilities.
- Promote a culture of challenge, escalation, and safe reporting.
Legislative Background:
- Formulated based on recommendations from the Parliamentary Commission for Banking Standards established post-2008 crisis.
- Legislation enacted in December 2013 and expanded in May 2016 to include all Financial Services and Markets Act (FSMA) authorized firms.
Evaluations and Outcomes:
- A 2019 FCA review reported clearer accountability among senior managers and a stronger culture of leadership and responsibility.
- A 2020 PRA evaluation highlighted the regime’s effectiveness in meeting its original goals in the context of dual-regulated firms.
PSD2: Innovating Payment Security
The revised Payment Services Directive (PSD2) represents a significant update to the European Union's regulatory framework on payment services, building on the foundation set by the initial Payment Services Directive (PSD) adopted in 2007. Its primary goals are to foster a more integrated and efficient European payments market, enhance payment security, and improve consumer protection.

Recent Developments:
PSD2 was officially adopted on 12 January 2016, with EU Member States required to transpose it into national law by 13 January 2018. The regulatory technical standards for strong customer authentication and secure communication were published on 13 March 2018 and came into effect on 14 September 2019. These standards are critical for ensuring the security of electronic payments and protecting consumer data, setting the groundwork for a transition period allowing payment service providers to align with the new requirements.
Implementation Phases:
- Initial Adoption: Directive entered into force in January 2016.
- National Transposition: EU Member States transposed PSD2 by January 2018.
- Regulatory Standards Effective: Implementation of technical standards by September 2019.
Components of PSD2:
- Strong Customer Authentication: Introduces requirements for multi-factor authentication to increase the security of electronic payments.
- Open Banking APIs: Mandates that banks provide third-party providers access to their customer's accounts through secure application programming interfaces (APIs), fostering innovation and competition.
- Enhanced Consumer Rights: Strengthens consumer rights, including immediate refunds on unauthorized transactions and a limit on customer liability for lost or stolen payment instruments.
Objectives and Impact:
- Market Integration: By standardising payments architecture across Europe, PSD2 aims to create a more cohesive European payments market.
- Increased Competition: Opens the market to new players, breaking down the monopoly of banks over their customer's data.
- Security Enhancement: Introduces stringent security measures for electronic payments and sensitive financial data protection.
- Consumer Protection: Enhances safeguards for consumers, ensuring immediate response to fraud and unauthorized use while setting limits on consumer liability.
ProCheckUp Solution's
UK-GDPR Compliance:
- IASME Cyber Essentials: A certification that verifies basic cyber-security hygiene, ensuring that financial institutions have fundamental security controls in place to protect against common cyber threats. (Learn More)
- IASME Cyber Assurance: This includes a GDPR readiness assessment to ensure that all aspects of data privacy and security are addressed, thus aligning with the GDPR’s stringent requirements.(Learn More)

For Data Protection Act 2018 Adherence:
- Data Protection Impact Assessments (DPIA): Services to help financial institutions conduct assessments that evaluate the impact of new projects or technologies on the privacy and security of personal data.(Learn More)
- Data Governance Consulting: Expert consultancy to ensure the correct handling of personal data across all operations, aligning with the Data Protection Act’s provisions.

For PCI-DSS Compliance:
- PCI-ASV (Approved Scanning Vendor) Services: ProCheckup, a globally recognized ASV, conducts meticulous external vulnerability scans to ensure the integrity of systems handling credit card data, in compliance with PCI-DSS requirement 11.3.2. Our ASV scan solution leverages cutting-edge security tools to rigorously test and confirm your network's defenses against known threats, helping to secure your data transactions. (Learn More)
- PCI-QSA (Qualified Security Assessor) Services: As an independent QSA firm accredited by the PCI Security Standards Council, ProCheckup embodies excellence in ensuring entities meet the stringent standards of PCI DSS. Our longstanding expertise, since the establishment of the QSA program, provides reliable validation of your compliance posture. (Learn More)
- Penetration Testing: ProCheckup's penetration testing services are an embodiment of our commitment to security excellence, meeting PCI-DSS requirement 11.4.1. Our team of Crest, Cyberscheme, and NCSC-qualified penetration testers, with a proven 24-year track record since 1999, employs a comprehensive approach to identify and remediate exploitable security vulnerabilities. (Learn More)
- Data Discovery for Primary Account Number (PAN): Our specialized services extend to the detection of PAN within your network, particularly identifying unauthorized storage locations outside the Cardholder Data Environment (CDE), adhering to PCI-DSS requirement 12.5.2. ProCheckup ensures that sensitive payment data is contained and managed securely. (Learn More)
- Segmentation Testing: With precise technical testing, ProCheckUp validates the efficacy of network segmentation, ensuring that the CDE is isolated from all systems not pertinent to card processing , in compliance with PCI-DSS requirement 11.4.5 This critical service supports PCI-DSS compliance by verifying the robustness of segmentation controls, maintaining the security of your cardholder data environment. (Learn More)
- Wireless Testing: Adhering to the stringent standards of PCI-DSS requirement 11.2.1, our team conducts comprehensive wireless testing quarterly. This process is meticulously designed to uncover and assess both sanctioned and unsanctioned wireless access points within your network, ensuring a robust security posture. (Learn More)

For CBEST Compliance:
- CBEST Intelligence-led Testing: Services that include simulating a targeted attack on financial institutions’ critical systems to assess resilience, as mandated by the CBEST framework.(Learn More)
- Threat Intelligence Services: Monitoring and analysis of potential threats specific to the financial sector, to prepare for and mitigate sophisticated cyber-attacks.

For Adherence to FCA Guidelines:
FCA Cyber Resilience Audits: A comprehensive review of cybersecurity practices against the FCA’s guidelines to ensure that vulnerabilities are identified and addressed.
Incident Reporting Mechanisms: Implementing and testing procedures for prompt incident reporting to the FCA in accordance with NCSC guidelines. (Learn More)

For SMCR Requirements:
- SMCR Compliance Software: Tools that help in managing the recording and handling of data related to personal accountability, ensuring it remains secure, especially within hybrid work models.
- Cyber security Leadership Training: Tailored training programs for senior managers to foster a culture of cyber resilience and to support decision-making processes regarding IT and cyber-security risks.

For PSD2 Compliance:
- API Security Testing: Assessing the security of APIs that are essential for open banking, ensuring they are resilient against cyber-attacks while allowing secure access by third-party providers.
- Strong Customer Authentication Solutions: Implementing multi-factor authentication processes that comply with PSD2’s requirements for secure customer authentication.

By integrating these cyber-security services, financial institutions can effectively navigate the complexity of regulatory compliance while fortifying their defenses against the cyber threats that endanger the sector’s integrity and stability. These services provide a scaffold for building a comprehensive cyber-security strategy that is not just about adherence to the letter of the law but also about embedding cyber-security into the fabric of financial services operations."
Maintaining Compliance
Implementing Robust Cybersecurity Frameworks
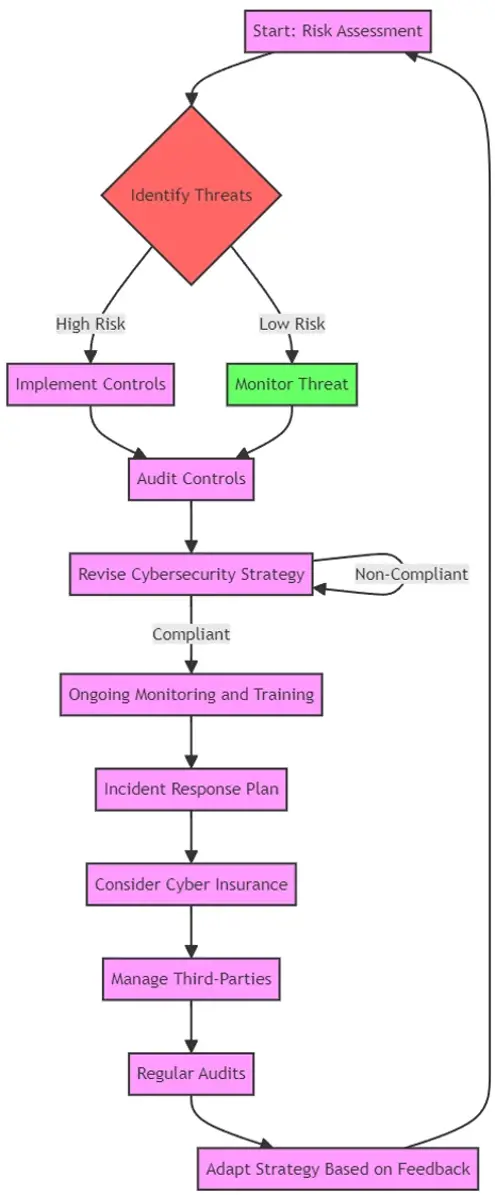
To keep up with the dynamic nature of cyber threats and regulatory requirements, financial services firms are encouraged to implement robust cyber-security frameworks that are responsive and adaptive. Here's an overview of what this involves:
- Risk Assessment and Management: Regular risk assessments to identify and prioritize potential threats, followed by the development of a risk management strategy that includes appropriate controls and mitigation tactics.
- Employee Training and Awareness: Continuous education programs for all staff members to recognize phishing attempts, manage sensitive data correctly, and understand their role in the organization's cybersecurity posture.
- Incident Response Planning: A well-structured incident response plan that outlines procedures for detecting, responding to, and recovering from cyber incidents to minimize impact and resume normal operations as quickly as possible.
- Technology and Access Control: Deployment of state-of-the-art cybersecurity technologies, alongside strict access controls to ensure that only authorized personnel have access to sensitive systems and data.
- Regular Audits and Compliance Checks: Conducting internal and external audits to ensure all cybersecurity measures are effective and in compliance with the relevant regulations.
- Investment in Cyber Insurance: Considering cyber insurance to mitigate financial losses from cyber incidents, which can also require organizations to maintain certain cybersecurity standards to qualify for coverage.
- Vendor and Third-Party Management: Ensuring that third-party vendors and partners also comply with cybersecurity standards to avoid breaches stemming from external sources.

Cybersecurity Process Flow Chart
Cybersecurity Collaboration and Sharing
In addition to the internal measures, it is crucial for financial services to actively participate in sector-wide cyber-security initiatives. These include:
- Information Sharing: Engaging in information sharing platforms such as the Financial Services Information Sharing and Analysis Center (FS-ISAC) to receive timely alerts on threats and share best practices with industry peers.
- Regulatory Engagement: Maintaining an open dialogue with regulators to stay ahead of new regulations and to influence policy development with real-world insights.
- Public-Private Partnerships: Partnering with government agencies to enhance the collective cybersecurity posture and respond more effectively to national security threats.
- Global Cybersecurity Standards: Aligning with global cybersecurity standards and frameworks, such as ISO/IEC 27001, to ensure a consistent approach to managing information security.
- Cybersecurity Advocacy: Advocating for stronger cybersecurity measures and more substantial investments in cyber-security at industry conferences and in public forums.

With these resources and strategies in place, financial services providers can better anticipate and counteract the evolving cyber threats they face, ensuring trust and continuity in the digital age.



Categories